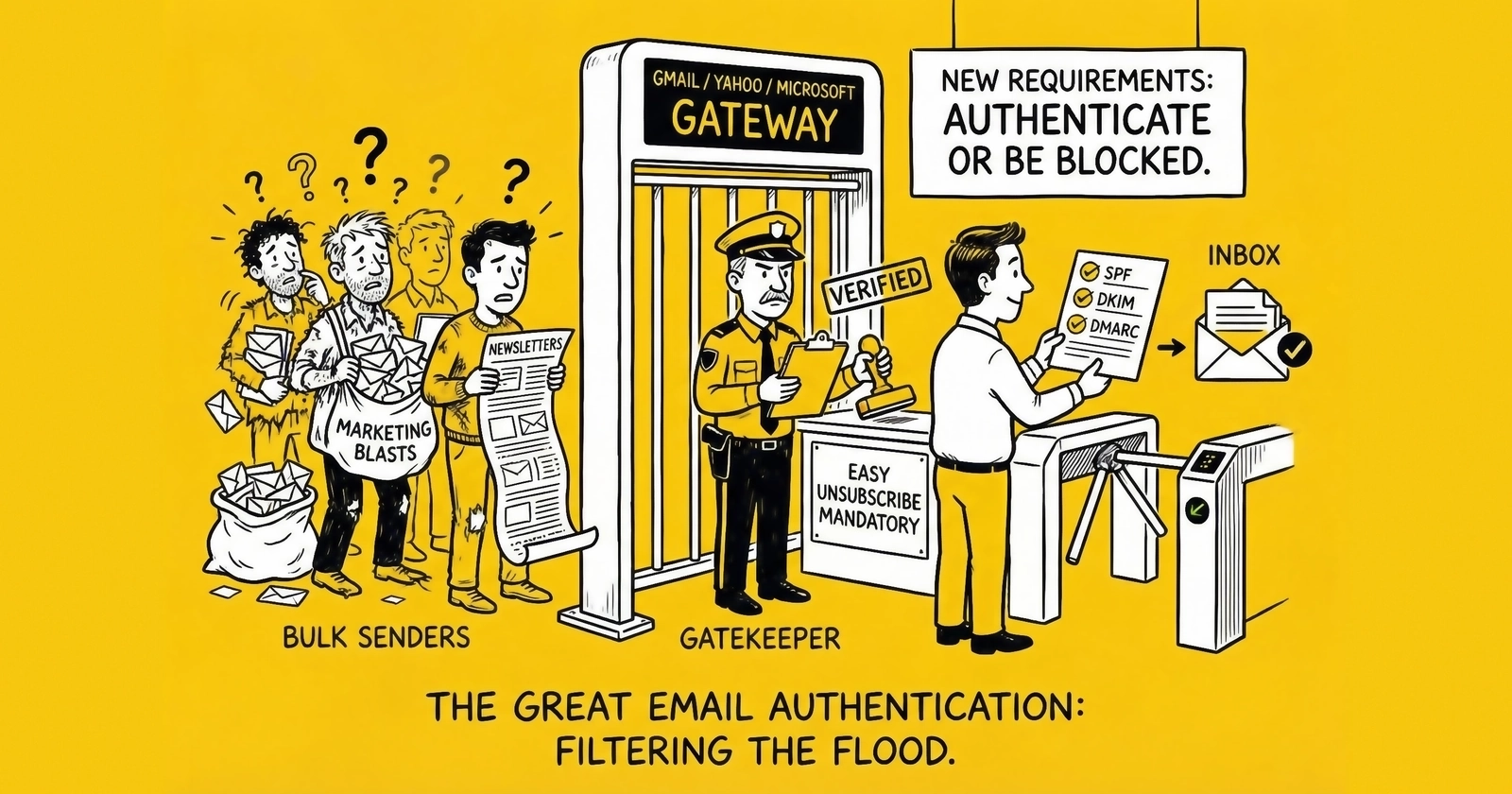
What changed in inbox enforcement, why lead gen operators get hit harder than most senders, and the operational rules for staying compliant at scale.
Email deliverability changed in February 2024 when Google and Yahoo moved authentication from “recommended” to “required” for bulk senders. What used to be a reputation gradient became something closer to a compliance gate: if you fail the requirements, your mail can be rejected outright.
The impact is operational, not theoretical. SPF/DKIM/DMARC failures translate into SMTP rejects. Complaint-rate violations translate into throttling and spam placement that can take weeks to unwind. Teams that treated email as a “campaign channel” discovered it behaves more like infrastructure: fragile when unmanaged, dependable when instrumented.
By 2025, Microsoft joined with similar requirements for Outlook.com consumer domains. The direction of travel is clear: providers are standardizing around the same baseline controls – authenticate identity, keep complaints low, make unsub frictionless – and enforcement is tightening, not loosening.
This guide focuses on what changed, what the requirements actually are, and how operators keep their sending programs alive under stricter enforcement.
Why Lead Generation Operators Get Hit Harder Than Most Senders
Lead gen programs are structurally high-risk because the mechanics of the business push you toward the exact patterns inbox providers punish. You often send at high frequency through multi-touch sequences. You often mail recipients who aren’t “newsletter warm” – lower intent, higher forgetfulness, more spam-button behavior. Your acquisition sources can shift overnight, which means list quality can shift overnight. And you frequently operate multiple domains and subdomains for tracking, brand separation, and warmup, which multiplies the chances that one sender drifts out of alignment.
That combination produces two distinct failure modes. The first is compliance: a new sender appears, DMARC alignment breaks, and mail starts rejecting. The second is reputation: you mail dormant cohorts or low-intent sources, complaint rates spike, and providers throttle or bury you in spam.
Treat the provider requirements as a floor, not a finish line. The operators who stay in the inbox build monitoring and change control around these rules, because the rules are not “set and forget.” For ongoing monitoring practices, see our guide to bulk sender compliance monitoring.
The Genesis of Bulk Sender Requirements
To understand where we are, we must first understand how we arrived here. Email authentication standards have existed for decades. SPF was formalized in 2006, DKIM in 2007, and DMARC in 2012. Yet adoption remained stubbornly low for years because implementation was optional and enforcement was minimal.
The tipping point came from an unlikely source: the sheer volume of malicious email threatening to overwhelm legitimate communication. By 2023, spam and phishing had reached epidemic proportions. Gmail alone was blocking over 100 million additional spam messages daily using AI-powered detection, yet the problem continued to grow. Sophisticated phishing operations were exploiting the lack of authentication enforcement to impersonate legitimate brands with alarming success.
On October 3, 2023, Google and Yahoo made a joint announcement that would reshape the email landscape. Starting February 1, 2024, bulk senders would face mandatory authentication requirements. This was not a request. It was an ultimatum with clear consequences for non-compliance.
Why Google and Yahoo Acted Together
The joint announcement was strategically significant. By presenting a unified front, Google and Yahoo made it impossible for senders to simply route around stricter enforcement by one provider. Together, these companies control the vast majority of consumer email addresses in the Western world. Gmail alone serves over 1.8 billion active users, while Yahoo and its associated properties (including AOL) maintain substantial market share.
The coordinated timing also sent a clear message to the industry: this was not an experiment or a test. This was the new reality, and adaptation was not optional. Organizations had approximately four months to achieve compliance before enforcement began.
Defining the Bulk Sender: The 5,000 Email Threshold
The cornerstone of the new requirements is the definition of a bulk sender. Google established a clear threshold: any entity sending 5,000 or more messages to personal Gmail accounts within a 24-hour period qualifies as a bulk sender and faces enhanced requirements.
This definition carries several critical nuances that organizations must understand. First, the count applies to the primary domain, which means all subdomains contribute to the total. An organization sending 2,500 emails from promotions.example.com and 2,500 from newsletter.example.com has sent 5,000 emails from example.com and qualifies as a bulk sender.
Second, and perhaps most importantly, the bulk sender classification is permanent. Once a domain reaches the 5,000 daily message threshold, it retains bulk sender status indefinitely. There is no expiration date and no mechanism for reclassification. An organization that sent 5,000 emails on a single day three years ago remains a bulk sender today, regardless of current sending volume.
Third, the requirements apply specifically to personal consumer mailboxes. Email sent to @gmail.com and @googlemail.com addresses falls under these requirements, but email sent to Google Workspace business accounts does not. This distinction is important for B2B senders whose primary audience uses corporate email addresses, though most organizations have mixed audiences that include personal accounts.
Yahoo’s Approach to Bulk Sender Definition
Yahoo took a deliberately different approach to defining bulk senders. Rather than establishing a specific numeric threshold, Yahoo uses more flexible language, referring to senders of “significant volume” without specifying an exact number.
Marcel Becker, Yahoo’s Senior Director of Product Management, explicitly addressed this distinction in public communications. He stated that “the number is not 5,000, or 6,000, or 4,000,” emphasizing that if an organization sends the same email to a lot of people, that organization is a bulk sender regardless of the specific count.
This intentional vagueness serves a purpose. It prevents senders from gaming the system by staying just below a specific threshold while still engaging in bulk sending behavior. Yahoo evaluates sending patterns holistically rather than against a single metric.
The practical implication for organizations is straightforward: if your sending behavior resembles that of a bulk sender, you should treat yourself as one regardless of exact volume. Attempting to optimize around thresholds is a losing strategy.
The 5,000 Threshold in Real Programs (Why “We Don’t Send That Much” Is Usually Wrong)
The 5,000 number feels large until you model it like an operator instead of a marketer.
Lead gen volume multiplies because outbound is not “one email per contact.” It is sequences. A single lead might trigger:
- a confirmation email
- a first follow-up
- a second follow-up
- a 3 – 7 day drip sequence
- transactional notices (appointment reminders, quote updates)
If you generate 800 leads per day and your average sequence is 7 touches, you are at 5,600 outbound messages before you add newsletters, reactivation, and internal system notifications. If multiple tools can send, you hit 5,000 without noticing.
This matters because bulk sender status is effectively permanent: once you cross the threshold, you should assume you will be treated like a bulk sender going forward. Build for compliance before your first big campaign forces you into it.
Technical Requirements for All Senders
Before examining the enhanced requirements for bulk senders, it is essential to understand the baseline requirements that apply to all email senders, regardless of volume. These foundational elements represent the minimum acceptable standard for any organization sending email to Gmail or Yahoo users.
SPF or DKIM Authentication
All senders must implement at least one of the two primary email authentication mechanisms: Sender Policy Framework (SPF) or DomainKeys Identified Mail (DKIM). For non-bulk senders, implementing either one is sufficient to meet this baseline requirement.
SPF works by publishing a DNS record that specifies which mail servers are authorized to send email on behalf of a domain. When a receiving server gets an email, it can check whether the sending server’s IP address matches the authorized list in the SPF record. This provides a basic level of assurance that the email originated from an authorized source.
DKIM takes a different approach, using public-key cryptography to create a digital signature for each email. The sending server signs the message with a private key, and the receiving server can verify this signature using a public key published in DNS. This confirms both the sender’s identity and that the message content has not been modified in transit.
Valid DNS Records
Both forward and reverse DNS records must be properly configured for sending mail servers. Forward DNS (A records) maps hostnames to IP addresses, while reverse DNS (PTR records) maps IP addresses back to hostnames. These records must be consistent and valid.
The importance of reverse DNS cannot be overstated. Many receiving mail servers perform reverse DNS lookups as a basic validation step. If the PTR record for a sending IP does not exist or does not match the forward DNS, the email may be rejected or marked as suspicious before any content analysis occurs.
TLS Encryption
Email transmission must occur over a TLS-encrypted connection. Transport Layer Security protects email content from interception during transmission between mail servers. While this has been a best practice for years, it is now a mandatory requirement.
Most modern email infrastructure supports TLS by default, but organizations using older systems or custom configurations should verify that opportunistic TLS is enabled and functioning correctly. Connections that fail TLS negotiation and fall back to unencrypted transmission may result in delivery failures.
RFC 5322 Compliance
All email messages must conform to RFC 5322, which defines the Internet Message Format. This standard specifies the required structure for email headers, including proper formatting of From, To, Subject, Date, and Message-ID fields.
Common violations include missing or malformed Message-ID headers, incorrectly formatted date fields, and invalid character encoding in headers. These technical violations may not have caused issues in the past, but stricter enforcement means they can now result in delivery failures.
No Gmail Impersonation
Senders must not impersonate Gmail in the From header. This means no email should be sent with a From address that appears to come from Gmail unless it actually originates from Gmail’s infrastructure. This requirement targets phishing attempts that try to appear as official Gmail communications.
Spam Rate Threshold
Perhaps the most impactful baseline requirement is the spam complaint rate threshold. All senders must maintain a spam rate below 0.3% as measured by user-reported spam complaints. The recommended target is significantly lower at 0.1% or below.
This metric is calculated by dividing the number of spam complaints by the number of emails successfully delivered to the inbox (excluding messages that were already filtered to spam). The calculation occurs daily, and sustained high spam rates have severe consequences for deliverability.
Enhanced Requirements for Bulk Senders
Organizations classified as bulk senders face a more stringent set of requirements beyond the baseline standards. These enhanced requirements reflect the greater potential impact that high-volume senders have on the email ecosystem.
Both SPF and DKIM Required
While non-bulk senders need only implement SPF or DKIM, bulk senders must implement both mechanisms. This dual requirement provides defense in depth, ensuring that even if one authentication mechanism fails or is compromised, the other remains functional.
The practical implementation requires publishing both an SPF TXT record listing authorized sending IPs and DKIM records containing public keys for each sending domain. Organizations using email service providers must ensure that both authentication methods are properly configured through their provider’s domain authentication workflow.
DMARC Record Publication
Bulk senders must publish a DMARC record for their sending domain. At minimum, this record must exist with a policy of p=none, which enables monitoring without affecting delivery. The DMARC record is published as a TXT record at _dmarc.domain.com.
While a p=none policy satisfies the minimum requirement, organizations should plan for progression to stricter policies. The industry is moving toward mandatory p=quarantine or p=reject policies, and organizations that proactively strengthen their DMARC posture will be better positioned for future requirements.
DMARC Alignment
Beyond simply publishing a DMARC record, bulk senders must achieve DMARC alignment. This means the domain in the From header must align with either the SPF-authenticated domain or the DKIM-signing domain.
Alignment can be either relaxed or strict. Relaxed alignment, which is the default, requires matching organizational domains, meaning a subdomain can align with its parent domain. Strict alignment requires an exact match between the domains. Most organizations operate with relaxed alignment, which provides sufficient flexibility for complex email infrastructure while still ensuring authentication integrity.
One-Click Unsubscribe Implementation
All marketing and promotional messages from bulk senders must include a one-click unsubscribe mechanism that complies with RFC 8058. This requirement goes beyond traditional unsubscribe links that lead to preference pages or require confirmation steps.
The RFC 8058 implementation requires specific email headers. The List-Unsubscribe-Post header must contain the exact value “List-Unsubscribe=One-Click”. The List-Unsubscribe header must contain a URL that accepts POST requests.
When a user clicks the unsubscribe button in their email client, the receiving server sends a POST request to the specified URL with the body “List-Unsubscribe=One-Click”. The sender must process this request and complete the unsubscription within 48 hours.
This requirement applies specifically to marketing and promotional messages. Transactional emails such as password resets, order confirmations, shipping notifications, and two-factor authentication codes are explicitly exempt from the one-click unsubscribe requirement.
Visible Unsubscribe Link
In addition to the RFC 8058 header-based mechanism, marketing messages must include a visible unsubscribe link in the message body. This link should be easy to find and clearly labeled, allowing recipients who prefer traditional web-based unsubscription to do so without difficulty.
Microsoft Consumer Domains: Similar Requirements, Different Failure Modes
Microsoft’s Outlook.com consumer domains follow the same strategic direction: authenticate identity, enforce complaint thresholds, and punish senders who don’t control their programs. The operational difference is that Microsoft’s ecosystem has historically been more sensitive to new or low-reputation senders, especially during warmup.
Microsoft’s baseline expectations for bulk senders include SPF, DKIM, and DMARC implemented with correct alignment; functional postmaster@ and abuse@ mailboxes for the domain; and valid reverse DNS for sending IPs, especially important for dedicated infrastructure.
If you run dedicated IPs, Microsoft SNDS provides additional visibility (complaint ranges, trap hits, filtering status). If you run shared infrastructure, you are mostly reading outcomes via your ESP’s bounce logs and dashboards, which makes list discipline and change control even more important.
One-Click Unsubscribe as a System Design Problem
The RFC 8058 header is the easy part. The hard part is that lead gen email rarely lives in one system.
The failure pattern looks like this:
- A recipient unsubscribes in your marketing platform.
- Your CRM or a secondary tool still has permission to send and continues mail.
- The recipient uses the spam button next time.
- Your complaint rate spikes and providers interpret it as “this sender ignores opt-outs.”
Operator approach:
Define what “unsubscribe” means (marketing-only suppression vs total suppression), centralize suppression across systems (a shared suppression list or a single consent service), treat a complaint as an immediate suppression event, and audit unsub propagation monthly – not after you get throttled.
The Spam Complaint Rate: Your Most Critical Metric
Among all the requirements and metrics that affect email deliverability, the spam complaint rate stands alone as the most consequential. This single number can determine whether your emails reach the inbox or vanish entirely.
Understanding the Calculation
The spam complaint rate is calculated as the number of users who mark your email as spam divided by the number of emails successfully delivered to the inbox. This is a crucial distinction: emails that were already filtered to spam before reaching the inbox are not included in the denominator.
For example, if you send 10,000 emails, 9,000 reach the inbox, 1,000 are filtered to spam, and 27 recipients mark your message as spam, your complaint rate is 27 divided by 9,000, or 0.3%. Note that the 1,000 spam-filtered messages are excluded from both the numerator (they cannot be marked as spam by users) and the denominator.
The Thresholds and Their Consequences
Google establishes two critical thresholds for spam complaint rates. The absolute ceiling is 0.3%. Exceeding this rate makes senders ineligible for any deliverability support or mitigation assistance from Google. This is not a temporary consequence but a sustained state that persists until rates improve.
The recommended target is 0.1% or lower. Senders maintaining rates in this range are considered good actors in the email ecosystem. They receive full deliverability consideration and access to support resources when issues arise.
The zone between 0.1% and 0.3% represents elevated risk. While delivery is not immediately impacted, senders in this range are on thin ice. Any spike in complaints could push them over the threshold with immediate consequences.
Why Spam Complaints Matter So Much
Spam complaints represent the most direct signal of recipient sentiment. When a user marks an email as spam, they are explicitly telling their email provider that they do not want to receive similar messages. This signal carries enormous weight in the algorithms that determine email placement.
From the mailbox provider’s perspective, every spam complaint represents a failure. The provider allowed an unwanted message to reach the inbox, degrading the user experience. Providers are highly motivated to prevent future failures, which means senders with elevated complaint rates face increasingly aggressive filtering.
The feedback loop is punishing. High complaint rates lead to increased spam filtering, which means only the most engaged recipients see future messages. Engaged recipients are less likely to complain, but the overall reputation has already suffered. Breaking out of this negative spiral requires sustained effort and often a fundamental reassessment of sending practices. For broader context on maintaining inbox placement, see our email deliverability best practices for 2026.
Strategies for Maintaining Low Complaint Rates
The most effective strategy for maintaining low complaint rates is sending email that recipients actually want to receive. This sounds obvious, but many organizations underestimate how quickly recipient sentiment can shift. The email that was welcomed last month may be an annoyance today if content quality has declined or frequency has increased.
List hygiene plays a critical role. Continuing to email recipients who have not engaged with your messages in months is a recipe for complaints. These disengaged subscribers may have forgotten they signed up, may no longer find your content relevant, or may simply have changed email usage patterns. Implementing sunset policies that reduce or eliminate mailing to chronically disengaged subscribers is essential.
Making unsubscription effortless reduces complaints. Many users mark email as spam simply because they cannot find or cannot be bothered to navigate an unsubscribe process. A prominent, functional unsubscribe link in every message gives recipients an alternative to the spam button.
Setting clear expectations at signup helps align recipient understanding with sender behavior. If users expect weekly newsletters and receive daily promotional blasts, complaints are inevitable. The signup process should clearly communicate what subscribers will receive and how often. Lead operations handling phone contact alongside email should apply similar clarity to consent documentation and disclosure.
Enforcement Timeline and Current Status
The enforcement of bulk sender requirements has proceeded through multiple phases, each escalating the consequences for non-compliance. Understanding this timeline provides context for the current state and signals the likely direction of future enforcement.
Phase 1: February 2024 Warning Period
Beginning February 1, 2024, Google and Yahoo initiated enforcement with a focus on education rather than punishment. Non-compliant messages received temporary 4xx error codes, indicating that the message could not be delivered at this time but might succeed if retried.
These errors were applied to a small percentage of non-compliant traffic, allowing senders to identify issues without losing all their email. The error messages included clear explanations of which requirement was not met, providing actionable guidance for remediation.
Phase 2: April to June 2024 Escalation
The grace period ended in April 2024 when Google began issuing permanent 5xx rejection codes for non-compliant messages. These rejections are final and cannot be overcome by retrying. Messages that fail authentication or other requirements are simply not delivered.
The one-click unsubscribe requirement deadline arrived June 1, 2024. After this date, marketing messages lacking proper RFC 8058 headers faced enhanced scrutiny and potential delivery issues.
Phase 3: November 2025 Full Enforcement
The most recent major milestone occurred in November 2025 with the activation of full enforcement. Google retired the V1 Postmaster Tools interface, including the familiar IP and Domain Reputation dashboards. These were replaced with a binary Pass/Fail compliance model that leaves no room for ambiguity.
Under this new model, senders either meet all requirements and pass, or they fail to meet one or more requirements and face consequences. There is no middle ground, no partial credit, and no appeals process for technical non-compliance.
Microsoft Joins the Coalition: May 2025
Microsoft’s entry into the enforcement coalition significantly expanded the scope of these requirements. Beginning May 5, 2025, Outlook.com consumer domains implemented similar authentication requirements with immediate rejection of non-compliant messages.
While Microsoft’s requirements closely mirror those of Google and Yahoo, their implementation includes enhanced AI-based detection that goes beyond basic authentication checking. Microsoft improved Business Email Compromise detection by a factor of six in Q1 2025 through behavioral analysis, signaling increasingly sophisticated filtering that authentication alone cannot overcome.
Consequences of Non-Compliance
The consequences for failing to meet bulk sender requirements range from temporary disruption to permanent exclusion. Understanding these consequences helps organizations prioritize compliance efforts and communicate the urgency of implementation to stakeholders.
Authentication Failures
Messages that fail SPF, DKIM, or DMARC authentication may receive temporary rejection codes during enforcement phases, followed by permanent rejection codes once full enforcement is active. Specific error codes help diagnose the issue:
- 4.7.27 or 5.7.27: SPF failure
- 4.7.30 or 5.7.30: DKIM failure
- 4.7.31 or 5.7.31: Missing DMARC record
- 4.7.32 or 5.7.32: From header misalignment
Spam Rate Violations
Exceeding the 0.3% spam complaint threshold triggers loss of access to deliverability support and mitigation resources. This means that when delivery problems occur, senders cannot work with Google to resolve them. The only path forward is to reduce complaint rates below 0.3% for seven consecutive days to regain eligibility for support.
Unsubscribe Compliance Failures
Marketing messages lacking proper one-click unsubscribe headers lose access to deliverability mitigations. Additionally, failing to honor unsubscribe requests within 48 hours can result in permanent support ineligibility and accelerated spam filtering.
The Cascade Effect
Perhaps the most insidious consequence of non-compliance is the cascade effect on sender reputation. Even temporary authentication failures or spam rate spikes leave lasting marks on domain reputation. These marks influence future filtering decisions, meaning that the consequences of non-compliance extend far beyond the immediate rejection of non-compliant messages.
Reputation recovery is possible but slow. Consistent compliance over weeks or months gradually rebuilds trust with mailbox providers. During this recovery period, organizations may see reduced inbox placement even for fully compliant messages as the reputation rebuilds.
What Enforcement Feels Like in Operations
In most organizations, deliverability failures are diagnosed backward. The symptoms show up in revenue metrics and CRM dashboards before they show up in email tooling.
Common “early” symptoms that are actually late are easy to recognize once you’ve lived through them. Lead follow-up sequences suddenly underperform and someone says “leads are worse this week.” Confirmation emails “sometimes” arrive because transactional is throttled or misaligned. Reply rates fall off a cliff while volume stays constant. Support tickets appear – “I never got the email.” By the time you see these symptoms, you’re not preventing an incident. You’re already in one.
By the time these appear, the provider has already made a decision about your mail stream.
Operator diagnosis starts earlier:
SMTP logs show new 4xx deferrals or 5xx rejects, often provider-specific. DMARC reports show a new sender or a sudden alignment drop. Complaint proxies – unsubscribe spikes and spam-folder placement on seed addresses – rise after a campaign change.
The key mental model: providers respond to patterns, not individual messages. One misconfigured sender can contaminate the reputation of an entire domain. One bad list cohort can spike complaints enough to trigger throttles that persist for weeks.
If you run bulk sending as a production system, enforcement becomes a set of known failure modes with known fixes. If you run it as “campaigns,” enforcement feels random and unfair.
Practical Implementation Guide
Moving from understanding requirements to implementing them requires a systematic approach. The following implementation guide provides a practical roadmap for achieving and maintaining compliance.
Step 0: Inventory Like an Operator
Most compliance failures are not caused by missing records. They are caused by unknown senders.
Before you touch DNS, build a sending inventory:
- every domain and subdomain that sends mail
- every vendor or system that sends from each domain (ESP, CRM, support, app notifications)
- which domains are used in the visible From and which domains are used for Return-Path/bounce handling
If you can’t answer “who is allowed to send from this domain,” DMARC rollout becomes a game of whack-a-mole.
Step 1: Audit Current State
Before making changes, document your current authentication configuration. Query your DNS for existing SPF, DKIM, and DMARC records. Identify all domains and subdomains used for sending email. Catalog all email service providers and marketing platforms that send on your behalf.
Use authentication testing tools to send test messages and verify that authentication is working correctly. Document any failures or misalignments that need to be addressed.
Step 2: Implement SPF
Create or update your SPF record to include all legitimate sending sources. Remember the 10 DNS lookup limit and plan accordingly. If you have many sending sources, consider SPF flattening tools that convert includes to IP addresses, or use subdomains to distribute the lookup burden.
Common SPF includes for major email service providers should be added: include:_spf.google.com for Google Workspace, include:spf.protection.outlook.com for Microsoft 365, include:sendgrid.net for SendGrid, and similar includes for other providers you use.
Step 3: Implement DKIM
Configure DKIM signing for each sending service. Most email service providers offer automated DKIM setup through CNAME records that they manage. For self-hosted infrastructure, generate 2048-bit RSA keys or Ed25519 keys and publish the public key in DNS.
Use unique selectors for each signing key to enable key rotation without disruption. Plan for regular key rotation every three to six months as a security best practice.
Step 4: Implement DMARC
Start with a monitoring-only DMARC policy: v=DMARC1; p=none; rua=mailto:dmarc-reports@yourdomain.com. This satisfies the minimum requirement while you gather data about authentication results across your email streams.
Monitor the aggregate reports (rua) to identify any legitimate sending sources that are not properly authenticated. Address these gaps before progressing to stricter policies.
Step 5: Configure One-Click Unsubscribe
Work with your email service provider or marketing platform to ensure RFC 8058 compliant headers are included in all marketing messages. Most major platforms now support this natively, but the feature may need to be explicitly enabled.
Test the unsubscribe mechanism by sending test messages and verifying that the headers are present and that the unsubscribe endpoint functions correctly.
Step 6: Set Up Monitoring
Register your sending domains with Google Postmaster Tools and Yahoo Sender Hub. These free tools provide visibility into your authentication rates, spam complaint rates, and delivery performance.
Establish regular review cadences to monitor these metrics. Weekly reviews are sufficient for most organizations, but high-volume senders may benefit from daily monitoring.
Step 7: Implement List Hygiene Processes
Establish processes for maintaining list quality. This includes validating email addresses at point of collection, implementing double opt-in for marketing signups, removing hard bounces immediately, and developing sunset policies for disengaged subscribers.
Regular list cleaning using email validation services helps identify and remove problematic addresses before they cause delivery issues.
Operator Checklists (What to Do Before You Send Volume)
The requirements are written like technical specifications. Operators need pre-flight checks.
Pre-Flight Checklist (Before a Big Campaign or a Reactivation)
- Confirm authentication still passes on a live test message (SPF, DKIM, DMARC alignment).
- Verify one-click unsubscribe headers are present for marketing mail.
- Validate the cohort if it is dormant (90+ days) or sourced from a new partner.
- Start with the most engaged segment first. Ramp volume; do not jump straight to full list.
- Watch deferrals and rejects during the first 24 hours. If throttles rise, slow down.
Change Checklist (Before DNS/Vendor Changes)
- Document the current state (records, selectors, Return-Path settings).
- Make changes in a controlled window with a rollback plan.
- Verify from multiple resolvers (propagation issues are common).
- Monitor DMARC and provider dashboards daily for a week after changes.
These are boring checks. They prevent expensive outages.
Looking Ahead: What Future Requirements May Bring
The current requirements represent a floor, not a ceiling. Industry signals suggest that stricter enforcement is coming, and organizations that position themselves ahead of requirements will enjoy competitive advantages.
DMARC Policy Escalation
The most likely near-term change is a requirement for stricter DMARC policies. Currently, p=none satisfies the minimum requirement, but this provides no actual protection against domain spoofing. Industry observers expect requirements to escalate to p=quarantine or p=reject within the next 12-24 months.
Organizations should proactively progress their DMARC policies toward p=reject. The progression should follow a measured approach: start with p=none to monitor, move to p=quarantine with a low percentage to test impact, gradually increase the percentage, and finally progress to p=reject when confident that all legitimate email is properly authenticated.
PCI DSS v4.0 DMARC Requirements
For organizations handling payment card data, PCI DSS v4.0 introduces explicit DMARC requirements that will become mandatory in 2026. These requirements specify that organizations must implement DMARC with a policy that prevents unauthorized use of their domains for sending email.
This regulatory requirement reinforces the direction of the industry and provides additional impetus for organizations to strengthen their DMARC posture.
No Auth, No Entry
The ultimate destination of current trends is a “No Auth, No Entry” policy where unauthenticated email is universally rejected. While we are not there yet, the trajectory is clear. Organizations that treat authentication as a compliance checkbox rather than a fundamental infrastructure requirement will find themselves increasingly marginalized.
Conclusion
The bulk sender requirements are not “email best practices.” They are the operating conditions for reaching consumer inboxes at scale.
Operators who treat these rules as infrastructure win twice:
- They avoid the obvious failure modes (alignment breaks, missing headers, unmanaged senders).
- They build monitoring and list discipline that keeps complaint rates low when volume and acquisition sources change.
The practical goal is not perfection. It is stability: a sending program that keeps landing when other teams are diagnosing “lead quality” problems that are actually deliverability outages.
Frequently Asked Questions
Do these rules apply to transactional mail?
Some requirements apply broadly (authentication and alignment), while others apply specifically to marketing mail (one-click unsubscribe). The mistake is assuming “transactional is exempt” and then sending transactional mail from an unauthenticated or misaligned domain. Providers don’t care what you call the message if your identity signals are broken.
What’s the fastest way to check if we’re compliant?
Send a live message to a test mailbox, inspect the authentication results, and confirm alignment:
- SPF: pass/fail, and which domain passed
- DKIM: pass/fail, and which domain signed
- DMARC: pass/fail and alignment
Then verify marketing messages include RFC 8058 headers and that your unsubscribe endpoint actually suppresses the recipient across all senders.
If we stay under 5,000/day, can we ignore this?
No. In practice, teams miscount volume and cross the threshold without realizing it. More importantly, providers are moving toward baseline enforcement for all senders. If you operate like a bulk sender (high frequency, repeated templates, low-intent recipients), you will be evaluated like one.
Is DMARC “p=none” enough?
It is enough to satisfy the minimum record-publication requirement, but it is not enough for protection. p=none is a monitoring state. Operators use it to inventory senders and fix alignment. The industry trend is toward stronger policies (quarantine / reject) over time, especially for domains that are heavily impersonated or that operate at high volume.
Key Takeaways
- Bulk sender enforcement turned authentication into required infrastructure, not “best practice.”
- The 5,000/day threshold is easy to hit in lead gen because sequences multiply volume; plan for bulk-sender rules before you cross it.
- Bulk senders need SPF + DKIM + DMARC with alignment; “records exist” is not compliance if alignment fails.
- Complaint rate is the constraint that ends arguments; treat 0.3% as a hard ceiling and <0.1% as the operating target.
- One-click unsubscribe (RFC 8058) is a system design problem in multi-tool stacks; centralize suppression and audit propagation.
- Run bulk sending like a production system: inventory senders, control changes, monitor daily during risk windows, and use checklists before volume spikes.
Sources
- Google Blog: Gmail Security Authentication and Spam Protection - Google’s October 2023 announcement of bulk sender requirements
- Yahoo Postmaster Blog: More Secure Less Spam - Yahoo’s coordinated announcement of authentication requirements
- Microsoft Tech Community: Outlook Email Sender Requirements - Microsoft’s May 2025 bulk sender enforcement announcement
- Google Email Sender Guidelines - Official Google documentation on authentication and bulk sender requirements
- RFC 8058: One-Click Unsubscribe - IETF specification for signaling one-click functionality in list email headers
- Yahoo Sender Best Practices - Yahoo’s official sender requirements and guidelines
- FTC Telemarketing Sales Rule - Federal compliance requirements affecting lead generation email programs