A tactical guide to recognizing, screening, and defending against the serial litigants who file 31-41% of all TCPA lawsuits, with practical strategies for lead generators navigating the most aggressive litigation environment in the statute’s 34-year history.
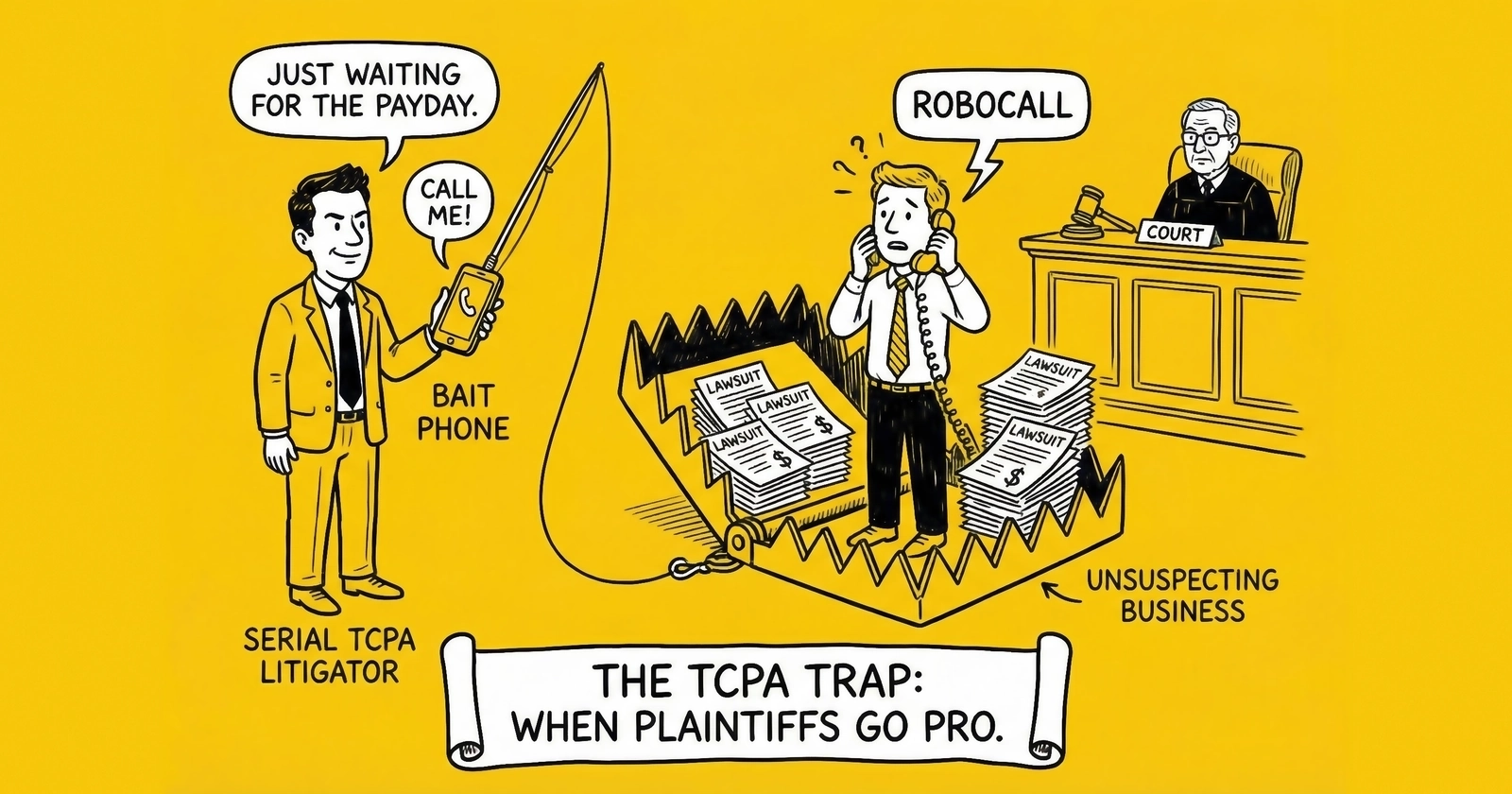
Introduction: The $6.6 Million Business Model
Somewhere in South Florida, a man maintains 47 active phone numbers across multiple carriers. Each number has been registered with lead generation forms across dozens of websites – insurance comparison sites, solar quote platforms, mortgage calculators, debt relief portals. He does not want insurance quotes. He is not buying solar panels. He has no interest in refinancing his mortgage.
He is farming TCPA lawsuits.
When a call arrives at 9:03 p.m. his local time – just three minutes past the legal calling window – he documents it. When a text message arrives without the proper seller identification, he screenshots it. When an autodialed call reaches a number he claims was reassigned to him, he files suit.
This man is not a hypothetical. He is one of hundreds of serial TCPA litigators who have turned consumer protection litigation into a lucrative profession. Analysis of 2024 filings reveals that between 31% and 41% of all TCPA lawsuits were filed by individuals who had previously filed TCPA suits. Some individual plaintiffs have filed dozens – even hundreds – of cases over multiple years.
For lead generation operators, these professional plaintiffs represent a distinct and manageable risk category. Unlike legitimate consumers who receive genuinely unwanted calls, serial litigators actively engineer situations that generate liability. They exploit every gap in compliance systems, every ambiguity in consent language, every technical failure in opt-out processing.
This article provides the operational framework for identifying these plaintiffs before they become your problem, implementing screening systems that reduce exposure, and defending against their claims when litigation materializes. The tools exist. The data is available. The question is whether you will use them.
Understanding the Serial Litigator Phenomenon
Who Are Serial TCPA Litigators?
Serial TCPA litigators are individuals who systematically generate TCPA claims as an income source. They differ from legitimate plaintiffs in their intent, methodology, and volume of litigation activity.
The typical legitimate TCPA plaintiff receives unwanted calls, becomes frustrated, and eventually files suit or joins a class action. They did not seek the calls. They did not engineer the situation. They simply want the calls to stop and believe they deserve compensation for the intrusion.
Serial litigators operate differently. They actively seek non-compliant communications. They create conditions likely to generate violations. They maintain detailed documentation of every potentially actionable contact. They have established relationships with TCPA plaintiff attorneys who file cases on contingency. Some have filed so many cases that they have become quasi-experts in TCPA litigation, occasionally representing themselves.
The economics are straightforward. A typical nuisance-value TCPA settlement ranges from $2,500 to $15,000 for an individual claim. A serial litigator filing 20 cases per year at an average settlement of $7,500 generates $150,000 annually – with minimal effort once the system is established. More sophisticated litigators targeting class action certification can generate significantly more.
The Scale of the Problem
The data on serial litigator prevalence reveals a significant industry vulnerability. Multiple analyses of TCPA litigation find that approximately one-third to two-fifths of all cases are filed by individuals with prior TCPA filing history – the 31-41% range reflects different methodologies for defining “repeat plaintiff.”
This concentrated plaintiff activity means a relatively small number of highly active litigators accounts for a disproportionate share of filings. Some individuals have filed more than 100 TCPA lawsuits over their litigation careers. Geographic concentration further compounds the problem: serial litigator activity clusters in jurisdictions with plaintiff-friendly procedural rules and experienced TCPA plaintiff counsel. South Florida has emerged as a particular hotbed, with some litigators maintaining strategic residence in the region.
Behind most serial litigators are attorney-litigator networks. Many work with a small number of plaintiff firms who specialize in TCPA claims. These firms provide the litigation infrastructure – filing, discovery, settlement negotiation – while the litigators provide the claims.
Why the TCPA Attracts Professional Plaintiffs
The TCPA’s structure makes it uniquely attractive for professional plaintiff activity. The statute provides $500-$1,500 per violation without requiring proof of actual harm. A single unwanted text message supports a claim worth $500 – regardless of whether it caused any real inconvenience. This statutory damages structure eliminates the need to prove injury.
The barrier to entry is remarkably low. Generating TCPA claims requires only phone numbers and the willingness to submit information to lead generation forms. No specialized knowledge or significant investment is needed. Attorney contingency arrangements mean litigators bear no upfront legal costs. Settlements often exceed the time invested in generating claims, particularly for experienced practitioners.
Once a litigator establishes a system – multiple phone numbers, form submission protocols, documentation practices – the marginal effort per additional claim is minimal. The process becomes repeatable and scalable. Even defendants with strong defenses often settle rather than incur $40,000-$50,000+ in defense costs. This settlement pressure creates reliable returns for litigators willing to file numerous claims. Courts rarely impose meaningful sanctions on TCPA litigators, even those with extensive filing histories. The risk-reward ratio strongly favors the plaintiff.
Serial Litigator Tactics and Techniques
Understanding how serial litigators operate is essential for building effective defenses. Their methods have become increasingly sophisticated as the industry has responded with screening tools.
Multiple Phone Number Strategy
Serial litigators typically maintain numerous phone numbers to maximize their surface area for receiving potentially non-compliant calls. Prepaid phones from different carriers provide multiple distinct numbers at minimal cost and can be activated quickly. Voice over IP services offer phone numbers at even lower cost, often with the ability to select specific area codes – a single litigator might maintain dozens of VoIP numbers. Some litigators extend their reach using phone numbers registered to family members or associates, expanding their claim-generation capacity while diversifying the plaintiff pool. The most sophisticated litigators deliberately acquire recently reassigned numbers – numbers that previously belonged to others who may have consented to calls. When calls arrive for the prior owner, the new owner claims they never consented.
Consent-and-Challenge Technique
This approach involves providing consent through lead generation forms while creating conditions that make the consent challengeable. Litigators submit information through forms with potentially non-compliant disclosure language, then challenge the consent in litigation. They exploit scope limitations by consenting to calls from one entity, then suing when affiliated companies or partners make contact – arguing the consent did not extend to those callers.
Revocation traps represent another variant: providing consent, then sending revocation requests through channels that may not be promptly processed – such as replying to an SMS with “stop” and waiting to see if additional messages arrive. Time-delay litigation involves waiting months or years after providing consent before filing suit, hoping that consent documentation will be difficult to retrieve or that systems will have changed.
Time-of-Day Exploitation
Federal law prohibits telemarketing calls before 8:00 a.m. or after 9:00 p.m. in the recipient’s local time zone. Serial litigators exploit this requirement by living in or claiming residence in time zones that make compliant calling hour calculations complex – particularly when mobile numbers have area codes from different regions. They pay close attention to calls received near the 8:00 a.m. or 9:00 p.m. boundaries, documenting any that arrive outside permitted hours. Daylight saving transitions present particular opportunity, as litigators file claims based on calls made when timezone calculations are particularly error-prone.
Reassigned Number Claims
When a phone number is reassigned from one consumer to another, the new owner has not consented to calls intended for the prior owner. Serial litigators exploit this through strategic number acquisition – obtaining numbers that appear to have been recently in use and are thus likely to receive calls based on the prior owner’s consent. They document all calls received to reassigned numbers, then file suit alleging the caller lacked consent from the current owner. Delays in reassigned number database updates create windows during which the number appears valid but has actually changed hands.
Documentation and Evidence Practices
Professional plaintiffs maintain meticulous documentation. Detailed call logs record every incoming call, including timestamp, caller ID, call duration, and any voicemail content. Text message archives preserve screenshots or exports with metadata about timing and sender. Form submission records include copies of lead forms submitted, along with screenshots of the consent language displayed – which they intend to challenge as defective. Records of complaints filed with the FCC, FTC, and state attorneys general establish a paper trail before litigation. Some experienced litigators develop relationships with technical experts who can testify about calling technology, ATDS definitions, and consent mechanisms.
Coordination with Plaintiff Attorneys
Serial litigators rarely operate in isolation. Most work with plaintiff law firms who provide case evaluation assessing which claims are worth pursuing and how to maximize recovery, filing infrastructure for complaint preparation and service of process, discovery management for written discovery and depositions, and settlement negotiation with defense counsel to achieve resolution. These firms take cases on contingency, typically retaining 33-40% of any recovery. The relationship is symbiotic: the litigator provides a steady stream of claims; the attorney provides legal expertise and shares in the recovery.
Identifying Serial Litigators Before Contact
The most effective defense against serial litigators is never contacting them in the first place. Identification and screening systems make this possible.
Litigator Suppression Lists
The industry has developed databases specifically designed to identify known TCPA litigators before calls are placed.
Contact Center Compliance (DNCScrub/Litigator Scrub)
Contact Center Compliance maintains one of the industry’s most comprehensive litigator databases, containing over 50,000 phone numbers associated with known TCPA plaintiffs. Their data is compiled from court records of TCPA filings across federal and state courts, demand letters received by their clients, attorney associations with known plaintiff firms, and pattern analysis of litigation behavior. The database is updated regularly as new filings occur, with integration available via API for real-time screening or batch processing for list cleaning.
PossibleNOW TCPA Litigator Database
PossibleNOW offers a complementary litigator screening service that tracks plaintiff identity across litigation history. Their data includes phone numbers associated with TCPA plaintiffs, name and address matching to identify plaintiffs across multiple numbers, filing history and pattern analysis, and attorney relationship mapping.
WebRecon Litigator Alert
WebRecon provides real-time monitoring of TCPA filings across jurisdictions. Their alerting service notifies subscribers when new cases are filed, enabling early identification of emerging serial litigators, tracking of litigation patterns by plaintiff and attorney, and market intelligence on litigation trends.
Gryphon Platform
Gryphon offers integrated compliance solutions that include litigator screening as part of a broader compliance stack, combining litigator database screening, DNC suppression, consent verification, and time-of-day enforcement in a unified platform.
Integration Best Practices
Effective litigator screening requires integration at multiple points in the lead lifecycle. At lead generation, screen phone numbers submitted through your own lead forms before the lead enters your database – this prevents known litigators from contaminating your lead flow at the source. At lead acquisition, before purchasing leads from third parties, screen the phone numbers against litigator databases; leads associated with known litigators should be rejected or excluded from purchase. Before calling, screen all numbers immediately before they enter the dialing queue to catch litigators whose information entered your system before screening was implemented or whose numbers were recently added to databases. For existing databases, periodically re-screen your entire lead database against updated litigator lists to identify numbers that become associated with litigation activity after initial acquisition for suppression from future contact.
Limitations of Suppression Lists
Litigator suppression is a critical defense layer, but it has inherent limitations. Suppression lists cannot identify someone who has not yet filed a TCPA lawsuit – first-time litigators will not appear in any database until after their initial filing. Serial litigators can obtain new phone numbers that are not yet associated with their litigation history; until that number is connected to a filing, it will not be flagged. If a litigator uses a different name or obtains numbers registered to others, identity matching may fail. There is always some delay between when a lawsuit is filed and when that information appears in suppression databases – calls made during this window can generate liability. Some suppression lists focus primarily on federal court filings, leaving serial litigators who file primarily in state court underrepresented.
For these reasons, litigator suppression should be viewed as one layer in a comprehensive compliance program – not a complete solution. It significantly reduces risk but does not eliminate it.
Building a Comprehensive Screening Program
Effective defense against serial litigators requires systematic screening that goes beyond litigator databases alone.
Multi-Layer Screening Architecture
The most robust screening programs operate on multiple dimensions.
Layer 1: Litigator Database Suppression
Screen all phone numbers against commercial litigator databases before any contact. This catches known serial plaintiffs with established litigation histories. Implementation involves API integration with litigator database providers, called at the moment leads enter your system and again before leads enter calling queues. This layer addresses approximately 31-41% of potential TCPA plaintiffs – those with prior filing history.
Layer 2: Do Not Call Suppression
Screen against federal and state Do Not Call registries plus internal suppression lists. While DNC suppression primarily addresses regulatory compliance rather than litigator avoidance, it also catches some serial litigators who register numbers specifically to generate DNC violation claims. Implementation requires integration with DNC.com, DNCScrub, or equivalent providers for registry access, along with maintenance of internal DNC lists for consumer opt-out requests. This layer addresses DNC-based claims, which represent a subset of serial litigator activity.
Layer 3: Reassigned Number Checking
Query the FCC’s Reassigned Numbers Database or commercial alternatives before calling numbers. This identifies numbers that have changed ownership, preventing calls based on the prior owner’s consent. Implementation involves API calls to the FCC RND or providers like Neustar before numbers enter calling queues. This layer addresses reassigned number claims, an increasingly common serial litigator tactic.
Layer 4: Pattern Analysis
Analyze lead submission patterns for indicators of serial litigator activity:
- Multiple form submissions from the same IP address with different phone numbers
- Form submissions that appear designed to generate defective consent
- Phone numbers with anomalous area code/location combinations
- Numbers associated with known VoIP providers commonly used by litigators
Implementation requires custom logic in your lead management system or integration with fraud detection services. This layer catches sophisticated litigators who evade name/number-based screening.
Layer 5: Consent Quality Scoring
Evaluate the quality and completeness of consent documentation before contact. Is a valid TrustedForm certificate or Jornaya LeadiD available? Does the certificate show clear, conspicuous consent language? Was the seller properly identified in the disclosure? Is the consent recent (within typical validity windows)? Does the certificate show suspicious activity such as unusual interaction patterns or possible bot behavior? Implementation involves integration with consent verification providers, with quality scoring rules that flag leads with consent deficiencies. This layer addresses consent-and-challenge tactics by ensuring only leads with robust consent enter calling queues.
Consent Verification Deep Dive
Strong consent documentation is your primary defense against both serial litigators and legitimate plaintiffs. The verification process should include certificate retrieval for every lead – retrieve the associated TrustedForm certificate or Jornaya LeadiD before contact, as unclaimed certificates expire and should be claimed at the time of lead purchase or generation.
TrustedForm provides session replay showing exactly what the consumer saw during the consent process. Review these replays – either through manual sampling or automated analysis – to verify that consent disclosure was visible and legible, the seller name matches the entity that will contact the consumer, consent was not a condition of purchase (no mandatory checkbox), and the phone number matches the number you intend to call.
Leads age. Consent obtained months or years ago may no longer be valid for current contact, particularly if the consumer has since revoked or if circumstances have changed. Establish maximum consent age thresholds based on your risk tolerance and calling patterns. Both TrustedForm and Jornaya offer signals indicating whether form submissions appear to come from real humans or automated bots – filter out leads with indicators of bot activity, as these cannot represent valid human consent.
Real-Time vs. Batch Screening
Screening can occur in real-time (at the moment of lead acquisition or calling) or in batches (periodic processing of lead databases).
Real-time screening prevents non-compliant leads from ever entering your system, provides immediate visibility into lead quality, and reduces exposure to the minimum possible window. However, it requires API integration with multiple providers, adds latency to lead processing, and may increase per-lead costs for API calls. This approach works best for high-volume operations where lead quality directly impacts profitability and for operations with sophisticated technology infrastructure.
Batch screening offers simpler implementation, lower per-lead cost for bulk processing, and the ability to retroactively clean existing databases. The drawbacks include delay between lead acquisition and screening that creates exposure windows, plus the need for careful queue management to prevent unscreened leads from being called. This approach suits operations transitioning to compliance infrastructure or lower-volume operations where real-time screening costs are not justified.
Most mature operations use a hybrid approach: real-time screening at lead acquisition to prevent contamination, pre-call screening as a final check before contact, and periodic batch screening to catch new litigator designations and clean aged data.
Defending Against Serial Litigator Claims
Despite best efforts, some serial litigator claims will materialize. Understanding how to defend against these claims is essential.
Early Case Assessment
When you receive a demand letter or complaint from a suspected serial litigator, conduct immediate assessment across four dimensions.
Begin with plaintiff research: search court records for prior TCPA filings by this plaintiff, query litigator databases for the phone number and plaintiff name, identify the attorney and research their TCPA filing history, and review any available information about the plaintiff’s litigation pattern.
Next, conduct a consent documentation review: retrieve all consent documentation for the phone number in question, claim and preserve any TrustedForm certificates or Jornaya LeadiDs, document the specific calls or texts at issue, and verify that your calling technology and procedures were compliant.
Calculate your exposure by determining the number of calls/texts to this plaintiff, calculating statutory exposure ($500-$1,500 per violation), assessing whether class allegations are viable, and estimating defense costs through various resolution points.
Finally, identify defenses: Is the plaintiff a known serial litigator? Can you prove valid consent? Does the calling technology qualify as an ATDS post-Duguid? Are there standing issues based on TransUnion v. Ramirez? Does the plaintiff’s conduct support any affirmative defenses?
Standing Challenges
Following the Supreme Court’s 2021 decision in TransUnion v. Ramirez, defendants have increasingly challenged plaintiff standing based on absence of concrete harm. Article III standing requires plaintiffs to show they suffered an “injury in fact” that is concrete and particularized.
The argument centers on the principle that receipt of an unwanted call or text, without more, may not constitute sufficient injury to establish standing. The plaintiff must demonstrate some tangible harm – wasted time, actual disruption, out-of-pocket costs – beyond the bare statutory violation.
Serial litigators are particularly vulnerable to standing challenges because they actively sought the communications (making claims of unwanted contact dubious), may have suffered no actual harm or disruption, demonstrate through their pattern of litigation that the calls were desired rather than resented, and maintain documentation practices suggesting preparation for litigation rather than genuine surprise.
Courts are split on standing challenges in TCPA cases. Some have dismissed cases where plaintiffs could not demonstrate concrete harm. Others have held that Congress’s creation of a private right of action itself establishes sufficient injury. Standing challenges are most viable in federal court, where Article III requirements apply; state court claims may not face the same hurdle.
Consent Defense
The strongest defense in any TCPA case is proof of valid consent. For serial litigators, this requires complete documentation including TrustedForm certificate or Jornaya LeadiD showing the consent transaction, session replay demonstrating what the plaintiff saw, proof that your company was identified in the consent disclosure, evidence that consent was not a condition of purchase, and documentation of the phone number consented.
You must also establish chain of custody: how the lead flowed from generation to your calling queue, what screening occurred at each step, when consent was verified, and who had access to modify lead data. Authentication evidence should include proof that the plaintiff actually submitted the form (IP address, device fingerprint), indicators that the submission was human rather than bot-generated, and any verification steps taken such as email confirmation or phone verification.
Serial litigators using the consent-and-challenge tactic may have genuinely provided consent – they just intend to challenge its validity. Strong documentation can defeat these challenges by proving exactly what happened during the consent process.
Revocation Defense Issues
The April 2025 FCC revocation rules create new defense considerations. Companies must honor revocation requests within ten business days – if you can prove you processed the revocation within this window, communications during the processing period may be defensible. Revocation can occur through “any reasonable manner”; if a serial litigator sends a revocation through an unusual channel specifically to create a delay, documenting your reasonable revocation procedures may support a defense. If evidence suggests the plaintiff deliberately used channels they knew would not be promptly processed, this pattern may support arguments about bad faith or lack of standing.
Serial Litigator-Specific Defenses
Some defenses are particularly relevant to serial litigator cases. The equitable doctrine of unclean hands may apply if the plaintiff engaged in deceptive conduct – such as providing consent with the specific intent to later challenge it, or manufacturing violations. Courts are generally reluctant to apply this defense in TCPA cases, but egregious litigator behavior may warrant its consideration.
Lack of causation arguments may exist if the plaintiff actively engineered the situation that led to the call – by providing consent through a form they knew was defective – suggesting the plaintiff, not the defendant, caused the violation. When a plaintiff has filed dozens of TCPA lawsuits, claims of genuine harm from receiving commercial communications become less credible. Discovery into the plaintiff’s litigation history and financial motivations can undermine damages claims.
Settlement Considerations
Most serial litigator cases settle. The settlement calculus differs from cases with legitimate plaintiffs.
Many serial litigator cases resolve for $2,500 to $15,000 – nuisance value settlements reflecting the cost of litigation rather than genuine liability exposure. These settlements are economically rational when defense costs would exceed settlement value. However, paying serial litigators creates a reputation for settlement willingness that can attract additional litigation. Some companies adopt policies of aggressively defending serial litigator cases to signal that they are not easy targets.
If you settle with a serial litigator, include strong confidentiality provisions preventing disclosure of settlement terms – this limits the plaintiff’s ability to use your settlement to attract additional cases. Ensure any settlement includes broad release language covering all phone numbers associated with the plaintiff, all claims under federal and state TCPA equivalents, all claims that could have been brought based on the same facts, and future claims for a specified period.
Litigation Strategy
When settlement is not appropriate and litigation proceeds, pursue aggressive discovery into the plaintiff’s complete TCPA filing history, financial benefits received from TCPA litigation, relationships with plaintiff attorneys, phone number acquisition and management practices, form submission patterns and intent, and documentation and evidence preservation practices.
Consider engaging expert witnesses in calling technology to address ATDS and prerecorded message issues, industry practices to establish compliance reasonableness, consumer behavior to challenge harm claims, and fraud detection to identify manufactured claims.
Share information with industry associations and other defendants. Serial litigators often target multiple companies; coordinated defense can be more effective than isolated response.
Vendor and Technology Requirements
Implementing effective litigator defense requires specific technology capabilities and vendor relationships.
Essential Technology Stack
| Function | Purpose | Key Providers |
|---|---|---|
| Litigator Suppression | Identify known TCPA plaintiffs | Contact Center Compliance, PossibleNOW, Gryphon |
| Consent Verification | Document PEWC for litigation defense | TrustedForm, Jornaya |
| DNC Suppression | Prevent calls to registered numbers | DNCScrub, DNC.com |
| Reassigned Number Checking | Identify changed number ownership | FCC RND, Neustar |
| Fraud Detection | Identify bot submissions and suspicious patterns | DataDome, PerimeterX, custom solutions |
| Litigation Monitoring | Track new TCPA filings in real time | WebRecon, PACER monitoring |
Vendor Evaluation Criteria
When selecting litigator screening vendors, evaluate database comprehensiveness: how many phone numbers are included, what sources feed the database (federal court, state court, demand letters), how frequently data is updated, and what geographic coverage exists.
Assess integration capabilities including API availability and documentation quality, batch processing options, CRM and dialing platform integrations, and response time for real-time queries.
Understand the match methodology: phone number matching accuracy, name/address matching for identity resolution across numbers, false positive rates (blocking legitimate leads), and false negative rates (missing actual litigators).
Verify compliance and support factors: data sourcing legality and compliance, customer support responsiveness, contractual protections and indemnification, and reporting and audit trail capabilities.
Cost-Benefit Analysis
Litigator screening costs money, but the investment pays for itself rapidly. Typical costs include litigator database access at $500-$2,500 per month for API access (varying by volume), per-query fees of $0.001-$0.01 per phone number screened, and integration development of $5,000-$25,000 one-time depending on complexity.
Compare these costs against risk exposure: average TCPA settlement with serial litigator is $7,500 (nuisance value), defense costs for an undefended case run $5,000-$10,000, and defense costs for a litigated case reach $40,000-$150,000 or more.
If litigator screening prevents just one case per month, the ROI is immediately positive. For operations with significant calling volume, the return is astronomical.
Consider an operation making 500,000 calls per month. Screening cost at $0.005 per number totals $2,500/month. If 0.1% of calls would have gone to serial litigators, that represents 500 potential plaintiff contacts. If 1% of those contacts generate litigation, that yields 5 cases per month. At $7,500 settlement per case, monthly exposure reaches $37,500. Net benefit of screening: $35,000/month minimum. The math strongly favors investment in screening infrastructure.
Building Organizational Defenses
Technology alone is insufficient. Organizational practices must support litigator defense.
Policy Development
Establish written policies addressing litigator screening requirements – when screening must occur (lead generation, acquisition, pre-call), which databases must be queried, how matches are handled (automatic suppression, manual review), and documentation requirements for screening results.
Define lead rejection criteria including conditions under which leads are rejected, handling of rejected leads (suppression, return to source, etc.), and communication with lead sources about rejection reasons.
Document consent quality standards covering minimum documentation requirements for lead acceptance, certificate verification procedures, age limits on consent validity, and handling of leads with deficient documentation.
Establish litigation response protocols specifying immediate actions upon receiving demand letter or complaint, escalation procedures and responsible parties, documentation preservation requirements, and external counsel engagement triggers.
Training Requirements
Train compliance staff on litigator identification techniques, screening tool operation and interpretation, consent verification procedures, and exception handling and escalation. Operations staff need training on recognition of suspicious lead patterns, proper documentation of screening activities, and escalation procedures for potential litigator contact. Legal and executive staff should understand the current TCPA litigation environment, serial litigator phenomenon and defense strategies, cost-benefit analysis of compliance investments, and settlement authority and strategy.
Audit and Monitoring
Implement ongoing monitoring to ensure policies are followed. Screening effectiveness audits should include regular review of screening hit rates, analysis of litigator contacts despite screening (false negatives), assessment of false positive rates (legitimate leads blocked), and database currency verification.
Consent documentation audits should involve random sampling of leads with consent verification, certificate retrieval success rates, quality assessment of documented consent, and gap identification and remediation.
Litigation pattern analysis should track TCPA claims received, analyze claim sources and patterns, compare to industry litigation trends, and identify emerging vulnerabilities.
Industry Response and Future Trends
The industry continues to develop responses to serial litigator activity. Understanding current initiatives and likely future developments helps operators prepare.
Current Industry Initiatives
Industry associations and informal networks facilitate sharing of litigator information. Companies that receive demand letters or complaints from serial litigators often share that information with industry peers, enabling broader suppression list coverage.
When serial litigators target multiple companies, coordinated defense can be more effective than isolated response. Sharing discovery, expert witnesses, and legal strategies reduces per-defendant costs and increases defense effectiveness.
Industry groups advocate for regulatory and legislative changes that would reduce serial litigator abuse: mandatory loser-pays provisions for frivolous TCPA claims, standing requirements that screen out manufactured harm, safe harbors for good-faith compliance efforts, and limits on statutory damages for de minimis violations.
Litigator database providers continuously enhance their offerings through faster incorporation of new filings, improved identity resolution across phone numbers, expanded state court coverage, and predictive analytics identifying likely future litigators.
Likely Future Developments
Some courts are showing increased skepticism of serial litigator claims, particularly regarding standing and manufactured harm. This trend may accelerate as the plaintiff population becomes increasingly dominated by professional litigators.
The FCC and Congress may eventually address serial litigator abuse through modified damages provisions, enhanced standing requirements, good-faith compliance defenses, or limits on repeat plaintiff recoveries. However, regulatory change is slow and uncertain. Operators should not wait for regulatory relief.
Screening technology will continue to improve: AI-powered pattern detection identifying likely litigators before they file, real-time integration across multiple data sources, blockchain-based consent verification providing stronger evidentiary trails, and biometric verification confirming human consent.
Serial litigators will adapt to industry defenses through new phone numbers and identities to evade suppression, more sophisticated consent-and-challenge tactics, targeting of companies with weak screening, and focus on emerging violation theories (revocation failures, reassigned numbers). The cat-and-mouse dynamic will continue. Sustainable defense requires continuous adaptation.
Frequently Asked Questions
1. What percentage of TCPA lawsuits come from serial litigators?
Analysis of TCPA litigation finds that 31% to 41% of cases are filed by individuals with prior TCPA filing history. The variation reflects different methodologies for defining “repeat plaintiff.” Some individual litigators have filed dozens or even hundreds of cases over multiple years.
2. How do litigator suppression lists work?
Litigator suppression lists are databases of phone numbers and names associated with individuals who have filed TCPA lawsuits. Providers compile this data from court records, demand letters, and pattern analysis. Companies query these databases before calling to identify and suppress numbers associated with known litigators.
3. What are the main providers of litigator suppression services?
The leading providers include Contact Center Compliance (Litigator Scrub), PossibleNOW (TCPA Litigator Database), WebRecon (Litigator Alert), and Gryphon. Each offers different features, coverage, and integration options.
4. Can litigator suppression lists identify all potential TCPA plaintiffs?
No. Suppression lists can only identify individuals who have previously filed TCPA lawsuits. First-time filers, litigators using new phone numbers, and plaintiffs who have not yet appeared in database sources will not be flagged. Suppression is one layer of defense, not a complete solution.
5. What tactics do serial TCPA litigators commonly use?
Common tactics include: maintaining multiple phone numbers to maximize claim opportunities; providing consent through forms and then challenging its validity; exploiting time-of-day calling restrictions; obtaining reassigned phone numbers to receive calls intended for prior owners; and documenting every potentially actionable contact for litigation.
6. How can I defend against a lawsuit from a serial litigator?
Key defenses include: researching the plaintiff’s filing history to establish serial litigator status; presenting strong consent documentation through TrustedForm or Jornaya; challenging standing based on lack of concrete harm (citing TransUnion v. Ramirez); pursuing discovery into the plaintiff’s litigation history and financial motivations; and, when appropriate, asserting defenses based on the plaintiff’s own conduct.
7. What is the typical settlement value for serial litigator cases?
Individual serial litigator claims often settle for $2,500 to $15,000 – reflecting nuisance value rather than genuine liability exposure. These settlements are economically rational when defense costs would exceed settlement amounts. However, paying settlements can create a reputation for settlement willingness that attracts additional litigation.
8. Should I pay nuisance settlements to serial litigators?
This is a strategic decision with no universal answer. Paying nuisance settlements may be economically rational in individual cases but can attract additional litigation. Some companies adopt policies of aggressively defending serial litigator cases to signal that they are not easy targets. Consider your litigation volume, defense resources, and risk tolerance.
9. How much does litigator screening cost?
Typical costs include: monthly access fees of $500-$2,500 depending on volume; per-query fees of $0.001-$0.01 per number screened; and one-time integration costs of $5,000-$25,000. For operations with significant calling volume, the ROI is strongly positive – preventing even one case per month justifies the investment.
10. What consent documentation best protects against serial litigator claims?
The strongest protection comes from third-party consent verification services like TrustedForm or Jornaya. These provide independent documentation including: timestamp and IP address; session replay showing exactly what the consumer saw; proof that your company was identified in the disclosure; evidence that consent was not a condition of purchase; and indicators of human (not bot) behavior.
Key Takeaways
-
31-41% of TCPA cases come from serial litigators. These professional plaintiffs have turned consumer protection litigation into a business model, systematically generating claims through multiple phone numbers, consent-and-challenge tactics, and exploitation of technical compliance requirements.
-
Litigator suppression is essential but incomplete. Commercial databases from Contact Center Compliance, PossibleNOW, and others can identify known litigators before you call them, but they cannot catch first-time filers or litigators using new numbers. Suppression is one layer in a multi-layer defense.
-
Strong consent documentation is your primary defense. TrustedForm certificates and Jornaya LeadiDs provide independent proof of what consumers saw and did during the consent process. Without this documentation, consent claims cannot be proven in litigation.
-
Multi-layer screening architecture reduces risk. Combine litigator suppression, DNC checking, reassigned number verification, pattern analysis, and consent quality scoring to catch threats that any single layer would miss.
-
Standing challenges are emerging as a defense. Following TransUnion v. Ramirez, defendants can challenge whether serial litigators who actively sought communications suffered sufficient injury to have standing. Courts are split, but this defense is particularly strong against plaintiffs with extensive filing histories.
-
Settlement decisions have strategic implications. Paying nuisance settlements may attract additional litigation. Some companies defend aggressively against serial litigators to signal they are not easy targets.
-
The math favors prevention. At $0.005 per number screened, litigator suppression costs a fraction of a single settlement. Operations with significant calling volume achieve astronomical ROI on screening investments.
-
Organizational practices must support technology. Policies, training, and auditing ensure that screening tools are used effectively and that documentation exists to support litigation defense.
-
The arms race continues. As the industry develops better defenses, serial litigators adapt their tactics. Sustainable protection requires continuous investment in screening technology, consent documentation, and compliance infrastructure.
-
Professional plaintiffs are a symptom, not the disease. Serial litigators exploit gaps in compliance systems. Closing those gaps – through better consent capture, cleaner calling practices, and robust documentation – addresses both litigator risk and legitimate plaintiff claims.
Build Your Defense Today
The serial litigator threat is real, quantifiable, and manageable. Between 31% and 41% of TCPA claims come from professional plaintiffs – individuals who have made a business of generating lawsuits. They are organized, sophisticated, and effective.
But they are not unstoppable.
Every tool described in this article exists today. Litigator suppression lists identify known plaintiffs. Consent verification services document valid consent. Screening integrations prevent contaminated leads from entering your system. Defense strategies have been proven in courtrooms across the country.
The question is not whether these defenses work. The question is whether you will implement them before a process server appears at your door.
The average TCPA class action settlement exceeds $6.6 million. The cost of comprehensive litigator screening is measured in thousands per month. The math is not complicated.
Choose your path wisely.
This article provides general information about TCPA compliance and serial litigator defense strategies. It is not legal advice. TCPA requirements change frequently, litigation strategies vary by jurisdiction and case facts, and state laws differ significantly. Consult qualified TCPA counsel for guidance on your specific situation.
Statistics current as of Q4 2025. Sources: WebRecon LLC litigation monitoring, Contact Center Compliance, industry sources.