The comprehensive guide to identifying, measuring, and mitigating risks that destroy lead generation businesses, from TCPA litigation to cash flow crises.
Introduction: Why Risk Management Separates Survivors from Statistics
The graveyard of lead generation businesses tells a consistent story. Not competition, not market shifts, not changing technology. The cause of death, in case after case: unmanaged risk that escalated from nuisance to existential crisis.
A mid-sized insurance lead generator in Florida received a process server’s knock in March 2025. The complaint alleged 47,000 TCPA violations. Potential exposure: $70.5 million. The company’s entire annual revenue was $12 million. This scenario plays out regularly across the lead generation industry.
Risk management in lead generation is not about avoiding all risk. That approach guarantees failure through inaction. Those who build lasting businesses understand that risk is inherent to value creation. Their advantage lies in identifying which risks matter, measuring their potential impact, and implementing systems that keep exposure within survivable bounds.
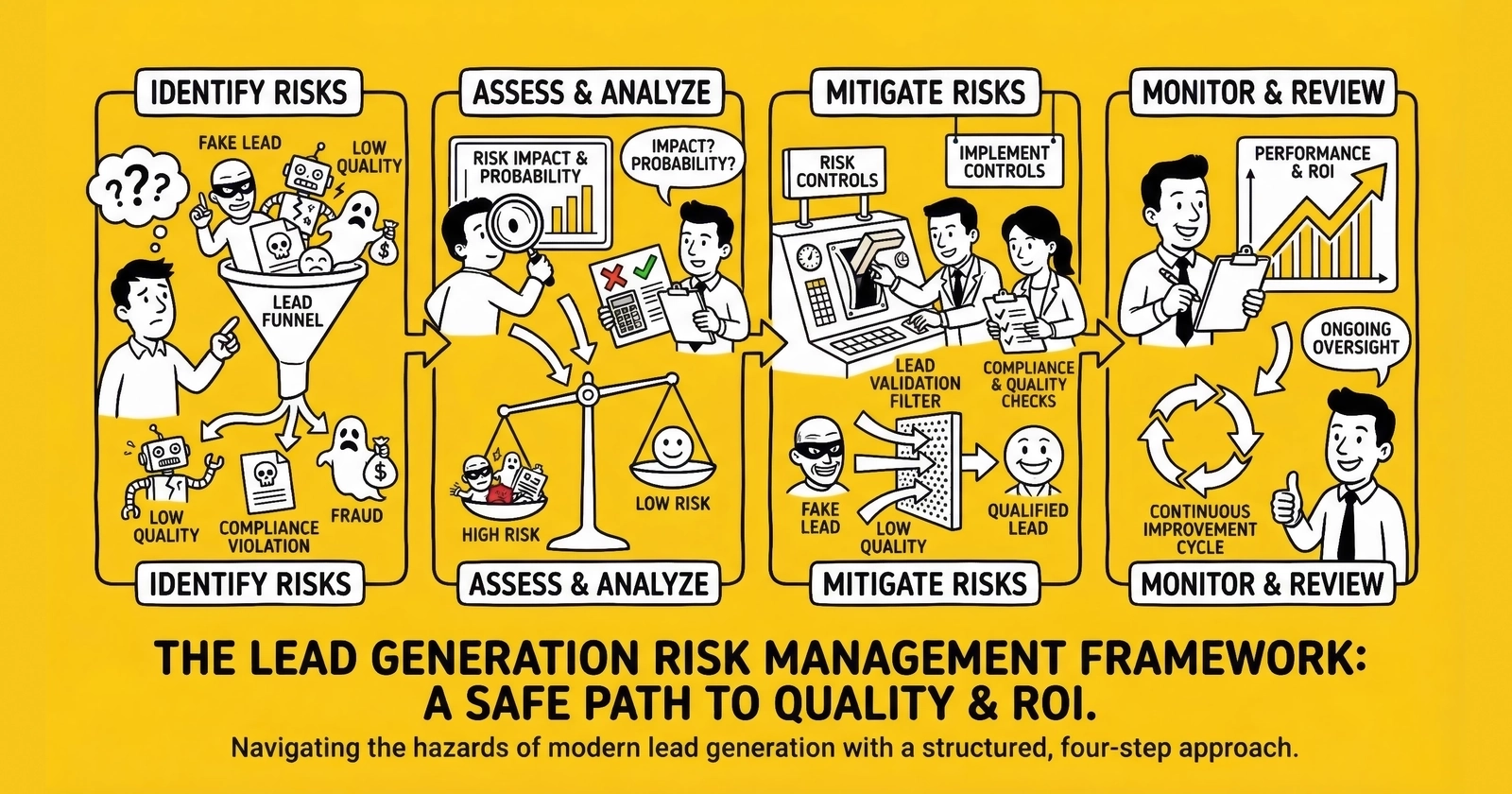
This article provides the complete framework. You will learn to categorize the major risk categories facing lead generation operations, quantify exposure using actual industry benchmarks, implement preventive controls that reduce probability without strangling growth, and build response protocols that minimize damage when prevention fails.
Those who master these disciplines build businesses that endure market cycles, regulatory shifts, and competitive pressures. Those who treat risk as someone else’s problem eventually discover it was their problem all along.
The Six Categories of Lead Generation Risk
Risk in lead generation clusters into six distinct categories. Each requires different monitoring systems, different mitigation strategies, and different response protocols. Understanding the taxonomy is the first step toward managing the whole.
1. Regulatory and Legal Risk
Regulatory risk dominates the lead generation risk landscape. The Telephone Consumer Protection Act (TCPA) has become, in the words of leading TCPA defense attorney Eric Troutman, “the biggest cash cow in history” for the plaintiff’s bar.
The statistics are staggering. In 2024, a total of 2,788 TCPA cases were filed, representing a 67% increase over 2023. The first quarter of 2025 alone saw 507 class action filings, a 112% increase year-over-year. By September 2025, class actions were running 97% ahead of 2024’s pace. Nearly 80% of all TCPA lawsuits are now filed as class actions.
The economics explain the litigation surge. Statutory damages of $500 to $1,500 per violation, with no cap on aggregate damages, create massive leverage for plaintiffs. A class action involving 10,000 leads creates exposure of $5 million to $15 million before defense costs. The average TCPA class action settlement exceeds $6.6 million. National Grid settled for $38.5 million (finalized in 2022). Citibank paid $29.5 million. Realogy settled for $20 million over trigger lead calls.
Beyond the TCPA, lead generators face an expanding patchwork of state-level regulations. Florida’s Telephone Solicitation Act (FTSA) creates stricter calling hour requirements (8 a.m. to 8 p.m.) and broader autodialer definitions. Oklahoma’s Telephone Solicitation Act (OTSA) adds call frequency limits. Maryland’s “Stop the Spam Calls Act” retains pre-Duguid autodialer definitions. Each state creates additional compliance obligations and litigation vectors.
The FCC continues evolving federal requirements. While the one-to-one consent rule was vacated by the Eleventh Circuit in January 2025, new revocation rules took effect in April 2025. Companies must now honor consent revocations within ten business days through any reasonable method. The standard opt-out keywords (stop, quit, revoke, opt out, cancel, unsubscribe, end) trigger immediate revocation obligations.
2. Financial Risk
Cash flow kills lead generation businesses more reliably than any competitor or market shift. Bank studies consistently show that 82% of small business failures stem from cash flow problems. In lead generation, the timing dynamics compound this vulnerability.
The fundamental challenge is float. Suppliers expect payment on NET 7 to NET 15 terms. Buyers typically pay on NET 30 to NET 60 terms, creating what’s known as the 60-day float rule. Some enterprise buyers stretch to NET 90. This creates a 30 to 75-day gap where you have paid costs but not collected revenue.
The math is unforgiving. An operation spending $50,000 per week on traffic acquisition and lead purchases must float $200,000 to $300,000 in working capital before receiving first buyer payments. Growth compounds the problem. Scaling 20% month-over-month increases float requirements 20% month-over-month. Many profitable operations fail not from inability to generate returns, but from inability to finance the cash gap created by their own success.
Return rates add uncertainty to already-tight economics. Buyer agreements typically allow returns within 7 to 14 days for specified reasons: duplicate leads, disconnected phones, invalid data, or leads that do not meet buyer criteria. If a buyer returns leads after you have paid your supplier, you bear the loss. Returns often cluster unpredictably, creating cash flow spikes that overwhelm under-reserved operations.
True margin calculations must account for all costs that platform-reported metrics ignore. A 40% gross margin on $50 purchase with $70 sale becomes approximately 16-17% net margin after returns (12% average), float costs ($0.80 per lead), duplicate leakage, bad debt, and processing fees. Operations that price based on gross margin eventually discover their “profitable” campaigns are break-even or worse.
3. Concentration Risk
Concentration risk manifests in two forms: buyer dependency and source dependency. Both can transform a healthy operation into a crisis overnight.
Buyer concentration is the more common danger. An operator with 50% or more of revenue from a single buyer is not running a lead generation business. They are running an outsourced marketing department without an employment contract. Industry analysis shows that 20% of buyers generate 80% of revenue for most lead operations. This Pareto distribution becomes problematic when the largest buyer represents survival-level volume.
The dangers of buyer concentration compound over time. Terms erosion occurs when a buyer who represents half your revenue knows they have leverage. They demand price reductions, longer return windows, faster delivery, more generous dispute resolution. You accept because you cannot afford to lose the volume. Each concession reduces margin and increases operational burden. Payment risk concentrates as well. If your largest buyer delays payment or fails entirely, the cash flow impact cascades through your entire operation. Strategic dependency develops as your product development, processes, and team structure optimize around your largest buyer’s requirements. When that buyer changes strategy or churns, your operation is built around assumptions that no longer apply.
Source concentration creates parallel vulnerabilities. If a single traffic source or lead supplier represents 30% or more of your volume, you are one algorithm change or quality degradation from crisis. Platform policy changes, account suspensions, or supplier business failures can eliminate supply you depended upon, with no warning and no replacement available.
4. Operational Risk
Operational risks arise from internal processes, systems, and people. They often develop gradually, becoming visible only when a specific failure triggers consequences.
Technology failures create immediate business impact. Lead distribution systems going offline means leads cannot be routed to buyers, generating losses measured in leads-per-minute during downtime. Integration failures break connections with sources or buyers, stopping lead flow until resolved. Data corruption or loss can destroy consent documentation, buyer relationship data, or financial records with no recovery possible.
Quality control failures accumulate before becoming visible. A source degradation might deliver 30% fraudulent leads without announcing itself. The problem hides in aggregate metrics that look acceptable until you analyze them properly. Industry research suggests that up to 30% of third-party leads may be fraudulent, with some estimates indicating only 25% of purchased leads are genuinely qualified prospects. Buyers eventually discover quality problems, often before you do. They see conversion rates and return patterns across their entire lead supply. When your leads underperform, buyers may not complain immediately. They reduce volume, tighten filters, or simply churn.
Human failures include errors by individual operators, inadequate training, and intentional misconduct. A media buyer who scales a campaign without monitoring quality can burn through budget on leads that will all be returned. A compliance analyst who misses a disclosure requirement can generate class action exposure. An employee with data access can steal lead data or sabotage operations.
Process failures involve breakdowns in workflows that seemed adequate at lower volume. Manual processes that worked for 1,000 leads per day become error-prone at 10,000 leads per day. Documentation gaps that never mattered become critical when litigation demands evidence. Quality checks that were thorough at low volume become superficial under time pressure.
5. Fraud Risk
Fraud is not a peripheral concern. It is a structural feature of the lead economy that must be factored into every calculation. Fraud detection and prevention requires layered defenses.
The scale of the problem is significant. Approximately 30% of third-party leads contain fraudulent or materially false information. Digital ad fraud accounts for $84 billion in annual losses globally. Synthetic identity fraud generates $35 billion in losses. Malicious bot traffic now accounts for approximately 37% of all web traffic, up from 32% in the prior year. Global fraud losses are projected to reach $41 billion or more in 2026, up from $37.7 billion in 2024.
Fraud types affecting lead generation include bot-generated leads (automated scripts filling forms with synthetic or stolen data), click fraud (competitors or malicious actors draining ad budgets), incentivized leads (real people submitting information for rewards rather than genuine interest), synthetic identities (fabricated personas combining real and fake data elements that pass validation), and recycled leads (old leads resold as fresh inventory).
Sophisticated invalid traffic now constitutes 78% of detected invalid traffic in financial services. The obvious bots and click farms are caught by basic filters, but advanced fraud evades traditional detection methods. Fraudsters use residential IP addresses, emulate human behavior patterns, and rotate identities to avoid detection.
The economic impact of fraud extends beyond direct losses. Fraudulent leads that reach buyers damage relationships through poor performance metrics. Returns from invalid leads erode margins. Compliance risk increases when fraud involves synthetic identities or stolen data. The downstream effects often exceed the direct cost of the fraudulent leads themselves.
6. Reputational Risk
Reputation in lead generation operates within a tight-knit community where word travels fast. Your reputation with buyers determines whether you receive volume commitments or fight for scraps. Your reputation with sources determines whether quality publishers send you traffic or avoid your forms. Your reputation with regulators determines whether you receive warning letters or enforcement actions.
Reputational damage accumulates through consistent quality problems. Buyers who experience high return rates or poor conversion share that information with peers. Sources that observe payment delays or disputes share information with other publishers. Industry conferences, online communities, and direct relationships all serve as channels for reputation information.
Reputational damage can occur suddenly through crisis events. A data breach exposing consumer information makes news and triggers buyer reviews. An FCC enforcement action becomes public record. A class action settlement appears in industry publications. Each event creates a reference point that affects future business relationships.
Recovery from reputational damage requires sustained performance over extended periods. A single quarter of improved quality does not erase years of problems. Rebuilding trust with buyers, sources, and the industry generally takes years of consistent execution without further incidents.
Quantifying Risk Exposure
Effective risk management requires quantification. You cannot manage what you do not measure. The following frameworks enable you to calculate exposure across major risk categories.
TCPA Exposure Calculation
Your TCPA exposure is a function of call or message volume, consent documentation quality, and litigation probability.
The basic formula is: Maximum Exposure = (Non-Compliant Contacts) x (Statutory Damages) x (Willfulness Multiplier)
Statutory damages are $500 per violation, trebling to $1,500 if the violation is willful or knowing. A four-year statute of limitations means exposure accumulates over extended periods.
For a practical calculation, consider an operation making 50,000 outbound contacts monthly. If 10% lack valid consent documentation, that creates 5,000 potential violations monthly. Over twelve months, exposure reaches 60,000 violations representing $30 million to $90 million in potential damages.
Expected loss calculation incorporates probability. Historical litigation rates suggest approximately 0.1% of consumer contacts result in complaints that escalate to litigation. Of those, class certification rates run approximately 80%. Settlement amounts average $6.6 million for class actions.
Your risk-adjusted TCPA reserve should be 1-3% of revenue for compliant operations, 5-10% for operations with documentation gaps, and higher for operations with known compliance deficiencies.
Cash Flow Risk Quantification
Cash flow risk calculation requires modeling your receivables-payables gap under various scenarios.
Base case: Map your actual payment timing. If you pay suppliers at Day 15 and collect from buyers at Day 45, you are floating 30 days of cost on average. Calculate your average daily cost, multiply by 30, and you have your base float requirement.
Stress case: Model a scenario where your largest buyer delays payment by 30 days (common when buyers face their own cash pressure) while your suppliers demand continued payment. Your float requirement may double.
Crisis case: Model your largest buyer defaulting entirely. Calculate the exposure that represents as a percentage of monthly revenue. If that percentage exceeds 25%, your concentration creates existential cash flow risk.
Working capital requirements by scale follow predictable patterns. Operations processing 10,000 leads monthly should maintain $150,000 to $200,000 in working capital. At 50,000 leads monthly, the requirement grows to $500,000 to $750,000. At 100,000 leads monthly, working capital needs exceed $1 million.
Concentration Risk Metrics
Measure concentration using the Herfindahl-Hirschman Index (HHI) or simpler percentage thresholds.
For buyer concentration, calculate the percentage of revenue from each buyer. If any single buyer exceeds 25%, you have dangerous concentration. If your top three buyers represent 75% or more of revenue, diversification is urgently needed.
For source concentration, calculate the percentage of leads from each source. If any single source exceeds 30%, you have dangerous dependency. If your top three sources represent 80% or more of leads, diversification should be a priority.
The concentration risk score can be expressed as: Concentration Risk = (Largest Relationship Percentage) x (Churn Probability) x (Revenue Impact)
A buyer representing 40% of revenue with 20% annual churn probability creates expected annual revenue impact of 8% from that single relationship.
Risk Mitigation Strategies
With risks identified and quantified, the next step is implementing controls that reduce probability and impact while preserving business opportunity.
Regulatory Risk Mitigation
Regulatory compliance is the foundation of sustainable lead generation. The following controls address TCPA and related regulatory exposure.
Consent Capture Controls
Document consent at the moment of capture using third-party verification services. TrustedForm certificates or Jornaya LeadiD tokens record not just that consent was given, but the exact form, language, timestamp, IP address, and consumer action. Retain this documentation for a minimum of five years, beyond the four-year TCPA statute of limitations.
Ensure consent disclosures meet all required elements. The consent must be in writing (electronic signature meeting E-SIGN requirements), signed by the person to be called, clearly authorize the specific seller to deliver telemarketing messages using automated technology, identify the telephone number, and not be a condition of purchase.
Implement dynamic consent disclosure when using comparison shopping or multi-buyer models. Display specific seller information at the moment of consent. While the one-to-one consent rule was vacated, many sophisticated buyers require one-to-one or near-equivalent consent as a condition of purchasing leads.
Pre-Contact Screening
Implement litigator scrubbing on every lead before contact. Services like Litigator Scrub and TCPA Litigator List maintain databases of known serial plaintiffs. Serial litigators, who account for 31-41% of TCPA filings, deliberately collect phone numbers and receive calls to generate lawsuits.
Suppress against the National DNC Registry and all applicable state registries before telemarketing calls. Maintain internal DNC lists and honor verbal stop requests immediately.
Query the FCC’s Reassigned Numbers Database or commercial equivalents to identify numbers that have changed ownership. Calling a reassigned number can create liability even though you had valid consent from the original number holder.
Enforce time-of-day restrictions based on the recipient’s time zone. The TCPA prohibits telephone solicitations before 8:00 a.m. or after 9:00 p.m. local time. State laws often impose narrower windows. Florida requires 8 a.m. to 8 p.m. Text messages are subject to the same timing restrictions as voice calls.
Revocation Handling
Process opt-out requests within ten business days as required by April 2025 FCC rules. Recognize all standard opt-out keywords and any other communication that reasonably conveys intent to stop receiving calls or messages.
Synchronize opt-out status across all communication channels and platforms within the ten-day window. Non-compliant contacts after revocation create exposure regardless of original consent validity.
Send confirmation messages within five minutes of opt-out requests if sending confirmation, ensuring no marketing content is included.
Vendor Compliance
Third-party vendors, particularly lead generators and call centers, represent significant TCPA exposure. Before engaging any vendor that will generate leads or make calls on your behalf, conduct due diligence covering their TCPA compliance policies, consent capture mechanisms, litigation history, insurance coverage, and willingness to provide indemnification.
Vendor agreements should include specific TCPA compliance obligations, requirements for consent documentation, audit rights, indemnification provisions, adequate insurance requirements, and termination rights for compliance failures.
Do not accept vendor certifications of compliance without verification. Audit vendor consent documentation regularly. A vendor’s assertion of compliance means nothing without the ability to verify against actual documentation.
Financial Risk Mitigation
Financial risk mitigation centers on maintaining adequate capital reserves and managing payment timing.
Capital Requirements
Maintain six months of operating expenses plus 20% buffer for unexpected costs. This is not conservative planning; it is survival math. Calculate your actual float requirement before launching or scaling. Model supplier payment terms, buyer payment terms, expected return rates, and growth trajectory.
Maintain separate reserves for returns. When buyers return leads, the revenue reversal often comes 30 to 60 days after you recognized and spent the income. A 10% return reserve, held separately from operating capital, provides buffer against this timing mismatch.
Payment Terms Management
Negotiate payment terms strategically. Faster payment from buyers is more valuable than lower prices. A buyer who pays NET 15 versus NET 30 reduces your float requirement by 50% on their volume.
Extend supplier payment terms where possible. Every day of float you eliminate is capital you do not need to raise or borrow.
Build relationships with lenders before you need them. Revenue-based financing, factoring, and lines of credit are available to lead generation businesses with documented cash flows. Establish these relationships when your business is healthy, not during crisis when lenders can detect desperation.
Return Rate Management
Track return rates by source at granular levels. A 10% overall return rate might combine 2% from your best source with 35% from your worst. Source-level visibility enables surgical remediation.
Cut low-quality sources aggressively. When source quality degrades, reduce volume immediately rather than hoping for improvement. The leads you do not buy from a poor source cost you nothing. The leads you do buy cost margin, buyer relationships, and operational attention.
Concentration Risk Mitigation
Concentration risk mitigation requires deliberate diversification built into business strategy.
Buyer Diversification
Establish a hard limit: no single buyer should represent more than 25% of revenue. For conservative practitioners, 20% is safer. This is not a target; it is a ceiling that shapes sales strategy.
Build buyer diversification into your business model from launch. Before scaling volume with your first buyer, identify and onboard backup buyers who can absorb that volume if the primary relationship fails.
Monitor concentration metrics actively. Your dashboard should show buyer concentration daily. When any buyer approaches 25% of volume, pause scaling with them until diversification catches up.
Cultivate buyer categories, not just individual buyers. Build relationships across carrier types, buyer models (exclusive, shared, aged), and purchase patterns (steady volume, burst buying, seasonal).
Source Diversification
Apply similar limits to source concentration: no single source should exceed 30% of volume. Monitor source concentration weekly.
Develop multiple traffic channels. If all your leads come from Facebook, a policy change or account suspension can eliminate your entire supply overnight. Build presence across Google, native advertising, organic content, and other channels appropriate to your vertical.
Maintain relationships with churned sources. Sources that stopped delivering may restart under changed circumstances. Keep quarterly contact and maintain integration readiness.
Operational Risk Mitigation
Operational risk mitigation requires infrastructure, processes, and monitoring systems.
Technology Resilience
Implement redundancy for critical systems. Lead distribution platforms should have failover capability. Data should be backed up with recovery procedures tested regularly.
Choose platforms that scale beyond current needs. The cost of migrating between platforms mid-growth exceeds the cost of starting with more capable systems.
Document integration specifications and maintain technical knowledge across team members. Key person dependency on technical knowledge creates risk when that person becomes unavailable.
Quality Control Systems
Build quality measurement into core systems from day one. Every lead should track source identification, acquisition cost, validation results, delivery outcome, buyer feedback, return status, and conversion data if available.
Implement buyer feedback loops systematically. Request conversion data, contact rate information, and quality scores from every buyer. Make data sharing a condition of doing business.
Monitor source-level metrics continuously. Implement automated alerts for return rate spikes, contact rate degradation, and conversion declines.
Process Documentation
Document critical processes in written form accessible to multiple team members. Operational knowledge that exists only in individual heads creates single points of failure.
Test processes regularly through audits and simulations. Annual compliance audits are insufficient for rapidly evolving operations. Monthly reviews with quarterly deep dives are more appropriate.
Fraud Risk Mitigation
Fraud prevention requires layered defenses that increase cost and complexity for fraudsters.
Lead Validation Stack
Implement phone validation to verify number authenticity, line type, and carrier. Dead numbers and VoIP lines from suspicious providers indicate fraud risk.
Add email verification to confirm deliverability and identify disposable or temporary email addresses commonly used in fraud.
Deploy IP intelligence to identify suspicious originating addresses, including data center IPs, known fraud networks, and geographic anomalies.
Use device fingerprinting to identify patterns of multiple leads from single devices, a common indicator of organized fraud.
Implement bot detection through behavioral analysis, CAPTCHA, and other mechanisms that differentiate human interaction from automated scripts.
A comprehensive fraud prevention stack costs approximately $0.30 to $0.50 per lead. On 10,000 monthly leads, that is $3,000 to $5,000. Without prevention, fraud rates of 15-30% on $50 leads cost $75,000 to $150,000 per 10,000 leads in direct losses, plus downstream costs from buyer returns and relationship damage. The math strongly favors prevention investment.
Source Monitoring
Track fraud indicators by source. Some sources deliberately include fraudulent inventory because volume metrics look better. They assume you will not track at source level.
Cut sources with elevated fraud rates immediately. A source with 5% fraud is worth far more than a source with 15% fraud, even at the same nominal CPL.
Building a Risk Management Framework
Individual risk mitigation strategies must combine into a coherent framework that operates across your organization.
Governance Structure
Establish clear ownership of risk management at the executive level. TCPA compliance, cash flow management, and operational risk should have named owners with authority to make decisions and budgets to implement controls.
Create a risk committee or regular risk review process. Monthly reviews of key risk metrics with quarterly deep dives into specific categories ensure ongoing attention without overwhelming daily operations.
Define escalation paths. When a risk metric exceeds thresholds, who must be notified? What decisions require senior approval? Clear escalation prevents both overreaction to minor variations and underreaction to genuine threats.
Monitoring Systems
Implement dashboards that surface key risk metrics to appropriate audiences.
Executive Dashboard
TCPA exposure estimate, updated monthly. Buyer concentration percentages, updated weekly. Cash position relative to float requirements, updated daily. Return rates trending versus historical baseline.
Operational Dashboard
Source-level quality metrics, updated daily. Consent documentation rates and audit results. Revocation processing compliance. Fraud detection rates by source.
Compliance Dashboard
Consent capture verification rates. DNC suppression confirmation. Time-of-day compliance. Revocation processing timing.
Response Protocols
Develop documented response protocols for predictable crisis scenarios.
TCPA Litigation Response
When a complaint or demand letter arrives, immediately preserve all relevant documentation. Do not delete anything. Engage specialized TCPA defense counsel, ideally from pre-established relationships. Conduct early case assessment covering exposure calculation, consent documentation review, plaintiff background check, and liability analysis.
Major Buyer Default Response
When a major buyer stops paying or indicates potential default, immediately assess cash flow impact and activate credit relationships if needed. Accelerate diversification efforts and evaluate contract termination rights.
Source Quality Crisis Response
When a source shows sudden quality degradation, pause volume immediately pending investigation. Retrieve and audit recent lead samples. Communicate with buyers who received affected leads. Determine root cause before resuming any volume.
Data Breach Response
Immediately contain the breach and preserve evidence. Engage specialized incident response and legal resources. Assess notification obligations under applicable breach notification laws. Communicate transparently with affected parties.
Frequently Asked Questions
What is the biggest risk facing lead generation companies in 2026?
TCPA litigation represents the largest single risk facing lead generation companies. With 2,788 cases filed in 2024 (up 67% from 2023), 507 class actions in Q1 2025 alone (up 112% year-over-year), and average settlements exceeding $6.6 million, regulatory exposure can create existential liability overnight. A single compliance failure can generate class action exposure that exceeds the lifetime revenue of the operation.
How much capital should a lead generation business maintain as reserves?
Lead generation businesses should maintain a minimum of six months of operating expenses plus 20% buffer for unexpected costs and opportunities. Working capital requirements vary by volume: operations processing 10,000 leads monthly need $150,000 to $200,000, operations at 50,000 monthly need $500,000 to $750,000, and operations at 100,000 monthly need $1 million or more. The timing gap between paying suppliers (NET 7-15) and collecting from buyers (NET 30-60) creates the float requirement that catches undercapitalized operators.
What percentage of revenue should come from a single buyer or source?
No single buyer should represent more than 25% of revenue, with 20% being a more conservative ceiling. No single source should exceed 30% of volume. Concentration beyond these thresholds creates dangerous dependency where a single relationship change can trigger business crisis. Monitor concentration metrics weekly and pause scaling with any relationship approaching limits until diversification catches up.
How can lead generators protect themselves from TCPA lawsuits?
TCPA protection requires multiple layers of controls. Document consent at capture using TrustedForm, Jornaya, or equivalent services that create independent verification. Implement litigator scrubbing to identify and avoid serial plaintiffs who file 31-41% of TCPA cases. Suppress against DNC registries before all telemarketing contacts. Enforce time-of-day restrictions based on recipient time zones. Process revocation requests within ten business days. Conduct regular audits of vendor compliance. Maintain relationships with specialized TCPA defense counsel before litigation arrives.
What is the cost of fraud prevention versus fraud losses in lead generation?
A comprehensive fraud prevention stack costs approximately $0.30 to $0.50 per lead, including phone validation, email verification, IP intelligence, device fingerprinting, and bot detection. On 10,000 monthly leads, this represents $3,000 to $5,000 monthly investment. Without prevention, fraud rates of 15-30% on $50 leads create direct losses of $75,000 to $150,000 per 10,000 leads, plus downstream costs from buyer returns and relationship damage. The return on fraud prevention investment is substantial and immediate.
How should lead generation companies handle consent revocation requests?
Following April 2025 FCC rules, companies must honor consent revocation within ten business days of receipt through any reasonable method the consumer chooses. Standard opt-out keywords (stop, quit, revoke, opt out, cancel, unsubscribe, end) must be recognized immediately. Any communication that reasonably conveys intent to stop receiving calls or messages must be honored. Revocation status must be synchronized across all communication channels and platforms within the ten-day window. Confirmation messages, if sent, must go within five minutes and contain no marketing content.
What insurance coverage should lead generation companies carry for regulatory risk?
Lead generation companies should carry errors and omissions (E&O) coverage with specific TCPA endorsements. Standard commercial general liability policies typically exclude TCPA claims. Work with insurance brokers who understand lead generation to obtain appropriate coverage. Policy limits should reflect potential class action exposure based on contact volume. Review exclusions carefully, as many policies exclude coverage for willful violations or claims arising from inadequate consent documentation.
How do you measure and track lead quality risk across multiple sources?
Track source-level metrics including return rates, contact rates, and conversion rates by source. A 10% overall return rate might combine 2% from your best source with 35% from your worst. Implement buyer feedback loops that share conversion data, quality scores, and rejection reasons back to source assessment. Set quality thresholds below which no source operates regardless of volume. Automated alerts should trigger for return rate spikes, contact rate degradation, and conversion declines at the source level.
What are the warning signs that a lead generation business has dangerous concentration risk?
Warning signs of dangerous concentration include any single buyer representing 20% or more of revenue, any single source providing 25% or more of leads, top three buyers representing 75% or more of total revenue, top three sources providing 80% or more of total leads, accepting progressively worse terms from largest buyer, inability to replace volume if largest relationship ends, and operational processes optimized around a single buyer’s requirements.
How should lead generation companies prepare for potential regulatory changes?
Stay connected to regulatory developments through industry associations, specialized legal counsel, and regulatory monitoring services. The FCC’s one-to-one consent rule, though ultimately vacated, signaled regulatory direction that prudent practitioners addressed regardless of the specific rule’s fate. Many sophisticated operations maintain stricter-than-required practices because they anticipate continued regulatory pressure. Build compliance infrastructure that can adapt to changing requirements. Allocate budget for ongoing compliance investment rather than treating it as a one-time expense.
Key Takeaways
-
TCPA litigation has reached historic levels with 2,788 cases filed in 2024, 507 class actions in Q1 2025, and settlements averaging $6.6 million. Treat compliance as core business infrastructure, not a legal checkbox.
-
Financial risk from cash flow timing kills more lead generation businesses than competition or market changes. Maintain six months of operating expenses plus 20% buffer, and understand the 30-75 day float gap between paying suppliers and collecting from buyers.
-
Concentration risk from buyer or source dependency creates existential vulnerability. No single buyer should exceed 25% of revenue, and no single source should exceed 30% of volume. Build diversification into your business model from launch.
-
Fraud affects approximately 30% of third-party leads in some form. A prevention stack costing $0.30-$0.50 per lead prevents losses of $75,000 or more per 10,000 leads at typical fraud rates.
-
Consent documentation using TrustedForm, Jornaya, or equivalent services provides litigation defense that cannot be reconstructed after the fact. Retain documentation for five years minimum.
-
Risk quantification enables appropriate resource allocation. Calculate TCPA exposure based on contact volume and consent quality. Model cash flow under stress scenarios. Measure concentration using percentage thresholds.
-
Response protocols should be developed before crises occur. Pre-establish relationships with specialized TCPA defense counsel. Document incident response procedures. Define escalation paths for risk metric breaches.
-
Risk management is not about avoiding all risk. It is about identifying which risks matter, measuring their potential impact, implementing preventive controls, and ensuring exposure remains within survivable bounds.
The Path Forward
Risk management in lead generation is not a department, a checklist, or a one-time project. It is an ongoing discipline that shapes every operational decision.
Those who build lasting businesses understand this reality. They invest in compliance infrastructure before they think they need it. They maintain capital reserves that seem excessive until the day they are essential. They diversify relationships even when concentration would be more efficient. They track metrics that reveal problems before those problems become crises.
Those who treat risk as someone else’s concern eventually discover the consequences. A TCPA class action that exceeds annual revenue. A cash flow crisis triggered by a single buyer’s payment delay. A quality problem that destroys buyer relationships built over years.
The choice is not whether to manage risk. The choice is whether to manage it proactively or reactively. Proactive management costs resources but preserves optionality. Reactive management costs more resources and often forecloses options entirely.
Build the framework now. Implement the controls systematically. Monitor the metrics consistently. Develop the response protocols before you need them.
The lead generation industry rewards operators who understand that sustainable profit requires managed risk. Build your business to be among those operators.
Statistics and regulatory information current as of late 2025. TCPA requirements evolve continuously. Consult qualified legal counsel for current compliance requirements specific to your operation.